Conspire offers networking that allows users to apply analytics to their job searches or any other social endeavor.

Tinder For Tech Jobs: 5 Apps Better Than LinkedIn
Tinder For Tech Jobs: 5 Apps Better Than LinkedIn (Click image for larger view and slideshow.)
Are you really making the most of your social network? If you needed an introduction to someone important to you, would you know which people in your network already knew that person? Of the hundreds of people in your social network, how many of them would actually do you a favor? Do you know that you are letting some of your relationships wither on the vine?
Conspire, a social networking tool, is bringing an analytics approach to juggling your many relationships, and it could help you land your next job, launch your own company, or if you're really inventive, I suppose, even get you your next date.
Conspire is what co-founder and CEO Alex Devkar calls a "giant, shared CRM for people."
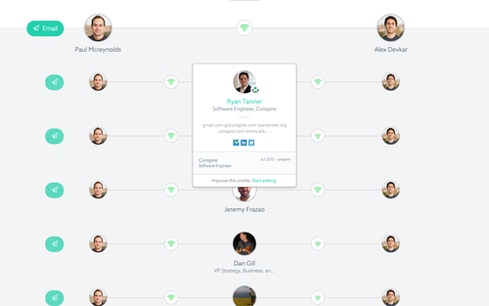
You enter your email addresses and Conspire pulls information from your contacts to form a picture of your social network (no "friending" or following required). Without reading the email (it just checks who you talk to, not what you say) it builds a picture of who you actually talk to. When added to the network information of other Conspire members, the company can build a giant picture of not only who you know, but who people you are connected with also know. A giant web of connections is born and continually added to as others join.
On the simplest level, in the end, what you get is a living version of the Kevin Bacon game or the 6 Degrees of Separation game.
Say you have a brilliant idea for a new company and you want to get funding for it, but you don’t want to go on Shark Tank. You can actually search for Mark Cuban (or anyone else) and it will tell you who you need to talk to who might introduce you to him. It turns out, I didn’t know it, but a friend of a friend knows Mark Cuban.
Of course, LinkedIn can do some of that. It can tell you who you know who might know someone at a company. But where the analytics comes in is that Conspire actually measures the quality of the relationships (depicted with icons similar to WiFi strength icons) so that you go to the right people.
Conspire measures how closely you are tied to people based on data like how often you communicate and how likely it is for you to respond to their email (or vice versa).
"If you try to do this on LinkedIn, they might show you 50 people who are two degrees away," said Devkar, "Of the 50 people LinkedIn names, you might not really know them very well. But we show you how to get this done. Because we understand the strength of relationship. If we see you send this person 100 emails and they never respond we know there is no relationship there."
In other words, you might be connected to hundreds if not thousands of people professionally. But which ones would really do you a favor? Who would vouch for you and connect you to people you know? Who could pick up the call and get your resume on the top of a stack? Of the two people you know who have met the hiring manager for the job you want, one met him once at a conference and one is in her fantasy football league. Do you know which is which?
Ultimately, Conspire is really only as good as the size of the network. The more members it has, the better it works. Conspire started as a way for startups to find venture capital and potential customers. But as the network grew, it has gone beyond the original capabilities. Basically, it is a people and relationship finder. It actually doesn't matter if you want to find the person because you want funding, a job, or you want to go on a date.
(Image: Conspire)
There is an interesting catch, however. For Conspire to work, it relies on networks. It builds those networks without the specific consent of everyone involved. For example, someone reading this article right now might have a Conspire profile without being a Conspire member. If you are in the contact list of a Conspire member, a profile of you has been built using public sources. Conspire members can edit your profile as well. So your picture, job title, contact information and other data may already exist on Conspire. Who you know and are good friends with might be there, too.
[ Read why everything you know about millennials is wrong. ]
Granted, most of that information is already public, and Conspire was quick to say that it has had no complaints about any breaches in privacy. But it isn’t hard to imagine some scenarios where it could be a problem. What if you were friends with someone recently convicted of a crime, or you were using your email to have an affair with someone? What if a journalist (those horrible journalists!) used it to get in touch with you to comment on the crime a friend committed because he or she sees you are close? Clearly, your exact relationship is not available, but your strong ties would be.
I foresee this as a hurdle Conspire will have to deal with as it grows.
As it is, though, it makes for an interesting tool. Just as you'd expect, the tool is only as good as your social network. And it is only as good as the network as a whole. Conspire readily admits that it will be more valuable for those in venture capital or technology right now than say, nursing. But as the network grows, the value will increase.
What do you think? Interested in applying a little analytics to your social networking? Think it could make a good side tool for your next job hunt? Let us know in the comments.
Attend Interop Las Vegas, the leading independent technology conference and expo series designed to inspire, inform, and connect the world's IT community. In 2015, look for all new programs, networking opportunities, and classes that will help you set your organization’s IT action plan. It happens April 27 to May 1. Register with Discount Code MPOIWK for $200 off Total Access & Conference Passes.
About the Author(s)
You May Also Like







