TruCrypt, PGP, FreeOTFE, BitLocker, DriveCrypt, and 7-Zip provide remarkably strong, on-the-fly, encryption to keep your data secure from loss, theft, or prying eyes.

Few IT professionals need to be lectured about data security. All too frequently we hear of the theft or loss of a computer or hard drive with data stored in the clear -- without encryption.
| |
| |
Fortunately, on-the-fly data encryption is no longer some exotic, costly beast. Rather than just encrypting single files, some applications are able to create virtual disks, either within a file or directly on a partition, where everything written to the disk is automatically encrypted. On modern hardware, the overhead for encryption is minimal; you no longer need dedicated hardware to make this happen.
In this review I've looked at several programs for creating and managing encrypted volumes, from Windows Vista's own BitLocker encryption to PGP's full-blown desktop suite for encrypting e-mail and instant messaging. You can even get remarkably strong, well-implemented whole-disk encryption without having to pay for it -- although in a corporate setting, features like manageability or support are well worth paying for.
1
TrueCrypt 5.1a
Cost: Free / open source
Web site: www.truecrypt.org
TrueCrypt makes an incredibly strong case for being the first whole-disk or virtual-volume encryption solution to try out. Aside from being free and open source (two big pluses), it's full of smartly written usability and data-protection features and is an effective way to encrypt a whole system, including the OS partition.
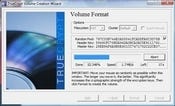
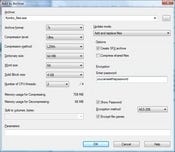
TrueCrypt lets you use your choice of AES, Serpent, and Twofish algorithms, either singly or in various combinations ("cascades"), along with the Whirlpool, SHA-512, and RIPEMD-160 hash algorithms. The actual encryption can work in one of three basic ways: it can mount a file as a virtual encrypted volume; it can turn an entire disk partition or physical drive into an encrypted volume; and it can encrypt a live Windows operating system volume, albeit with some limitations.
Encrypted volumes can be protected with a password and optionally a keyfile for additional security -- for instance, a file on a removable USB drive, which lets you create a form of two-factor authentication. If you create a standalone virtual volume, you can use a file of any size or naming convention. The file is created by TrueCrypt itself and then formatted to ensure that it appears to be nothing more than random data.
TrueCrypt is designed in such a way that no encrypted volume or disk can be casually identified as such. There is no obvious volume header, required file extension, or other distinguishing mark. The one exception is encrypted boot volumes, which have the TrueCrypt boot loader -- but it wouldn't be impossible in future versions of the product to conceal the entire volume and use an external boot loader from a USB thumb drive or CD. On that note, it's also possible to create a self-encrypted USB drive which runs in "traveler mode" -- it contains a copy of the TrueCrypt executable and can be mounted and run on any Windows machine where the user has admin privileges.
TrueCrypt also includes what it bills as "plausible deniability" features, the most significant being the ability to hide volumes inside each other. The hidden volume has its own password, and there's no way to determine if a given TrueCrypt volume has a hidden volume somewhere in it. If you write too much data to the outer volume, however, there's a chance you can damage the hidden one -- but, as a protection measure, TrueCrypt optionally lets you mount the hidden volume as read-only when mounting the outer volume.
If you're using system-disk encryption, the actual encryption process takes a while, but it can be suspended and resumed on demand (you may want to do it overnight with the PC in a locked room), and the program insists on creating a rescue CD that can be used to boot the computer in the event of a disaster. (One disadvantage: you can't encrypt a Windows system that's dual-booted from a non-Windows bootloader.)
2
Windows Vista BitLocker
Cost: Included with Vista Ultimate and Vista Enterprise
Web site: technet.microsoft.com/en-us/windowsvista/aa905065.aspx
| |
| |
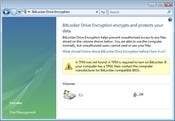
Vista's BitLocker, available only with the Enterprise or Ultimate versions of Vista, is specifically designed to perform system-volume encryption. It's not primarily designed for encrypting removable volumes, and it doesn't let you create virtual encrypted volumes like the other products described in this review. But it's been created with central management in mind, via Active Directory and Group Policy.
Unlike TrueCrypt's system-disk encryption, setting up BitLocker requires that you have at least two volumes in the target system -- one to hold the boot loader and a second one to hold the encrypted system files. An existing system can be re-partitioned using the BitLocker Drive Preparation Tool (now offered as an extra for systems that support BitLocker), but if you're working with an unprepared system, you can set up the partitions manually as well.
When you encrypt a volume with BitLocker, you're offered three basic choices for how to authorize the user to access the encrypted volume. If the computer has a TPM (trusted platform module), that can be used in conjunction with a PIN code. A second option is to create a removable USB drive that contains the authorization data and use that in conjunction with a PIN, although this only works if the computer in question can boot from a USB-connected device. If you elect to use this option, BitLocker will perform a boot test to ensure that your system can start from a USB device before encrypting the disk. The third option is to only have the user punch in a PIN, although this PIN will be quite long (upwards of 25 characters) and can only be assigned by the operating system.
As with any other full-disk encryption system, the slowest part is actually encrypting the drive; my 75-Gbyte notebook took about three-and-a-half hours to encrypt. Fortunately, BitLocker can do this in the background while other work is being accomplished, and you can even shut the system down and resume the encryption process later if need be. (My suggestion: Leave the computer in a locked room overnight.) The encryption keys for a given volume can also be saved to an Active Directory repository if an administrator needs to access or decrypt a volume. If you're not in an AD domain, you can also back up the keys manually to a file -- which should, of course, be protected closely.
Finally, while BitLocker originally protected only the operating system volume, it's possible to also manually encrypt non-system volumes with it through Vista's command line interface.
3
Dekart Private Disk 1.2
Cost: $45 per seat
Web site: www.dekart.com
While functionally similar to other encryption programs, Dekart Private Disk sports at least one feature that makes the program frankly unrecommendable.
For starters, Private Disk's feature set is only marginally more useful than either of the free / open source products described here. The user can create virtual encrypted volumes, back up the volume header for an encrypted disk, control the mounting or unmounting of disks based on user activity, and so on. The only really significant feature that isn't available elsewhere is the "Disk Firewall," which lets you grant or deny access to the encrypted volume to specific programs.
The biggest sign that Private Disk has not been written with real security in mind is a "recovery option" that attempts to determine the password of a private disk by performing a brute-force attack on the password. No serious encryption product would ever have something like this. It's like buying a deadbolt for your front door and discovering that it comes with a set of lockpicks -- "in case you lose the keys."
It's hard to give the nod to a for-pay program of this kind when the vast majority of its features are available for free elsewhere, and are probably better implemented there to boot.
4
DriveCrypt
Cost: 59.95 Euros ($88.73) per seat
Web site: www.securstar.com
| |
| |
SecureStar's DriveCrypt has core functionality similar to TrueCrypt and FreeOTFE, reviewed below -- you can create encrypted containers from files or whole disks, hide encrypted drives inside each other, and so on. For more advanced functionality, like whole-disk encryption, you'll need to add the DriveCrypt PlusPack ($185). Whether or not the additional features that DriveCrypt offers are worth paying for is an open question, since many people might be just as comfortable with the feature sets in the free products.
Most of the encryption functions in the standard DriveCrypt behave as you would expect if you've had experience with similar products. You can create virtual encrypted disks in either files or partitions, automatically lock disks after a certain period of inactivity, and create invisible disk-within-a-disk arrangements. DriveCrypt also lets you mount disks created by earlier iterations of the product (ScramDisk and E4M), so if you're migrating from either of those programs you won't be out in the cold.
Some functions available here that aren't offered by the free products are the ability to freely resize an existing encrypted disk and administrative key-escrow services. (The latter is possible in TrueCrypt and FreeOTFE by manually backing up the volume headers, though.)
Another feature specific to DriveCrypt: you can create a "DKF access file," which allows a third party to access an encrypted volume without needing the volume password. The DKF key can have various restrictions applied to it -- it can use its own password unrelated to the one on your own disk, expire after X days, or only work between certain hours. This makes it possible to provide a degree of controlled access to an encrypted drive.
Note that by default the program uses the partition id 0x74 to mark whole partitions that have been encrypted -- which makes it easier for the program to recognize and mount an encrypted partition, but also means it's that much easier for a potentially hostile third party to know that a given volume is DC-encrypted. Fortunately, you can defeat this behavior by setting a program option... and you probably should, since you're the only one who ought to know what's an encrypted container and what's not.
DriveCrypt's most intriguing feature is the ability to turn a .WAV file -- whether ripped from a CD or created from scratch -- into a steganographically encrypted container. Either 4 or 8 bits per sample can be used to store the data, so a 700-Mbyte .WAV file (the length of a music CD) can be used to store either 350 Mbytes or 175 Mbytes. The resulting file will still play, although the audio quality will be affected to some degree. (Caveat: It's probably not a good idea to use music from a readily available CD, as an attacker could compare your file against a rip from the CD to determine if hidden data is present, even if they can't decipher it. A voice recording might be better.)
5
FreeOTFE 3.00
Cost: Free / open source
Web site: www.freeotfe.org
| |
| |
In many ways FreeOTFE (OTFE meaning "on-the-fly encryption") is quite similar to TrueCrypt -- it offers many of the same features with some slight variations on their deployment, and it's also offered under a highly liberal software license.
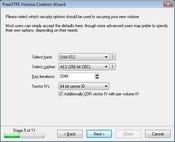
The process of creating a new volume is, again, similar to TrueCrypt: there's a wizard that walks you through the process and provides you with relevant options at each step. There's a slightly broader set of choices for the length of the volume salt and the hash, cipher, key, and disk-sectoring systems, although for most people the default choices will be fine. Some options are provided mainly for backwards compatibility, like the now-antiquated MD2 and MD4 hash functions -- use SHA512 or better for newly created disks.
One nice feature that TrueCrypt doesn't seem to offer is the ability to run arbitrary scripts after a volume mount and both before and after a volume dismount -- for instance, to perform cleanup of temporary files or other forensic scrubbing. Another handy function for Linux users is the ability to work with native Linux file system encryption drivers, such as Cryptoloop, dm-crypt, and LUKS.
Like TrueCrypt, you can also elect to create a separate keyfile, although the mechanism is a little different. TrueCrypt's keyfile for a volume can be any file at all, since it's used in a read-only fashion. FreeOTFE creates a keyfile from scratch to store a volume's metadata block, which could be placed on a USB key as a way to provide further physical security. When generating the random data for the new volume, the user can opt to employ the Microsoft CryptoAPI, data garnered from mouse movements for additional randomness, or both.
Also, like TrueCrypt, FreeOTFE can be used to hide one encrypted volume inside another, but the process for doing so is a little complicated. The user needs to manually specify a "byte offset" value that describes where the hidden volume will be located. If you don't know the offset value (and the hidden volume password), you won't be able to mount the hidden volume at all. This also makes it possible to hide an encrypted volume within an un-encrypted volume, albeit with some difficulty.
There's a strong emphasis on portability with FreeOTFE. User settings for the app can be saved either to the user's own profile or in a global fashion (i.e., to the program directory). Also, as with TrueCrypt, FreeOTFE features a "portable mode" -- a way to place the FreeOTFE executables and encrypted volume on a removable disk so it can be used on another computer, even one that doesn't have FreeOTFE installed. Finally, FreeOTFE is also available for Windows Mobile 6-based PDAs; volumes created or used on the desktop can be used on a PDA and vice versa.
6
PGP Desktop Professional
Cost: $199 per seat
Web site: www.pgp.com
| |
| |
PGP Desktop provides a whole suite of encryption tools that are designed to integrate as elegantly as possible with a Windows system, regardless of the application mix (although there are a few exceptions to that rule). It's best for those who are looking for comprehensive encryption coverage and are willing to pay a bit for something full-featured.
The program's main interface has five basic sections: key management, messaging, compression, disk management, and NetShare. The key management section is where you'll probably get started -- you can create new encryption keys, import existing ones from an external keyring, publish keys to PGP's global key directory (and search for other keys there as well), and so on.
Messaging controls how PGP Desktop deals with e-mail. Out of the box, PGP Desktop can encrypt standard SMTP/POP e-mail, Exchange/MAPI mail, and Lotus Notes mail. Instead of modifying the e-mail client, PGP Desktop proxies and monitors e-mail traffic in both directions and acts as needed. Messages sent to you that have been encrypted with a key in your keyring will be decrypted automatically. You can also create policies that describe how mail is to be intercepted and encrypted -- for instance, mail to all but a particular domain can be sent in the clear. The IM encryption system (which also works through a local proxy) supports only AOL Instant Messenger and Trillian; other programs that use AIM's protocols may work but PGP can't vouch for them. IM encryption uses 1024-bit one-time RSA keys for each logon; messages are encrypted with AES 256-bit symmetric keys.
The PGP Zip tab lets you create encrypted archives, which can be extracted with PGP at the other end or packaged as self-extracting archives. The resulting archive can also be signed and encrypted with either a passphrase or a recipient's key (if they have one). The whole PGP suite isn't needed for just creating password-protected and encrypted archives -- you can use many standalone compression apps to do that -- but the signing and key-usage features are generally not found elsewhere.
PGP Disk is the suite's whole-disk or virtual-volume encryption solution. Virtual volumes work a lot like TrueCrypt or FreeOTFE: the volume can be in any file, although with PGP the volume(s) in question can be encrypted (using AES, CAST5, or Twofish) with a user key as well as protected with a passphrase.
If you use whole-disk encryption, there's a couple of options you can select during the encryption process: maximum CPU utilization, to save time; and power-failure safety options to keep the system from getting trashed if the lights go out during the encryption process. Encrypted disks can use TPM hardware (if you have it), USB flash drives to store a keyfile, or some combination thereof. Another bonus feature included with PGP Disk is a data shredder tool, similar to the freeware Eraser product, which can erase files or simply scrub an existing disk's free space.
The NetShare feature (available in the PGP Desktop Storage and PGP Desktop Corporate editions) lets you share encrypted files on a portable drive or net-connected drive. All the decryption takes place at the user's end, so nothing sensitive is ever transmitted in the clear, and no special software is required on the file server. NetShare can also integrate with Active Directory for finer-grained management over who can access what. It's also possible to encrypt individual files outside of a designated protected folder, although this feature needs to be enabled separately (it's not on by default).
PGP Desktop isn't limited to working as a standalone application -- it can be managed by a central PGP server application (PGP Universal) in an enterprise setting. This makes PGP Desktop Professional a good choice if you plan to start using it on individual systems and later migrate to something more centrally controlled.
7
7-Zip
Cost: Free / open source
Web site: www.7-Zip.org
| |
| |
You might not think of the open source archiving application 7-Zip as a program that would fit in with the others described here, but it's actually a fine choice if you're simply looking for a quick-and-dirty way to create an encrypted, password-protected archive. 7-Zip can create self-extracting archives as well, so the recipient doesn't need to have 7-Zip -- just whatever password you've agreed upon. There's no native support for any kind of two-factor authentication, however. Also, for added security, be sure to select the "Encrypt file names" option when creating the archive.
Recommendations
Most people who want a basic disk-oriented solution will want to give TrueCrypt (or its close cousin FreeOTFE) a spin, especially now that the former provides whole-disk, boot-volume encryption. PGP Desktop adds many other tools as well, making it a good choice for those who want to branch out from just on-disk encryption into things like e-mail and protected messaging. BitLocker's big advantage is the fact that it's a native Vista feature and can be centrally managed through Active Directory; and DriveCrypt has some potentially useful steganographic and access-management features. 7-Zip is a simple way to create an encrypted, password-protected archive. Sadly, Dekart Private Disk is hard to take seriously as an encryption solution since it includes an absurd feature for brute-forcing volumes you've entrusted to the program's protection.
About the Author(s)
You May Also Like