As cyber espionage grows quickly, government agencies become the No. 1 target, finds 2014 Data Breach Investigations Report.
Government agencies are the most frequent target for cyber espionage, a type of attack that, though small in absolute numbers, is growing quickly, according the latest Data Breach Investigations Report from Verizon.
Public sector organizations accounted for 75% of the more than 63,400 security incidents reported worldwide, according to Verizon security researchers' findings in the 2014 Data Breach Investigations Report.
The high number of government incidents are skewed by US reporting requirements, which produce a "vast amount of minor incidents" that are not a sign of higher targeting or weak defenses, according to the report's authors. But they provide important clues about the evolving nature of security incidents.
One development masked by the overall numbers is a threefold increase in cyber espionage incidents in this year's report compared with last year's. The figures reflect a larger data set of reported espionage incidents, not necessarily a direct increase in attempts. But because such incidents are hard to discern, and can take months to uncover, the larger reported number of incidents still represents a concern.
[NIST's cyber security framework gives critical-infrastructure operators a new tool to assess readiness. But will operators put this voluntary framework to work? Read: Protecting Critical Infrastructure: A New Approach.]
"We're seeing a steady uptick in cyber espionage," says Bryan Sartin, director of the Research, Investigations, Solutions, Knowledge (RISK) team at Verizon Enterprise Solutions.
Espionage is considered "not significant" as a source of government security incidents because it accounted for less than 1% of the total. Because of the large number of other security incidents reported by government -- including insider misuse (24%), crimeware (21%), and theft or loss (19%) -- espionage does not appear on the statistical radar screen.
"This is relative," Sartin said, because in absolute terms the number of espionage incidents still is small compared with other types of incidents.
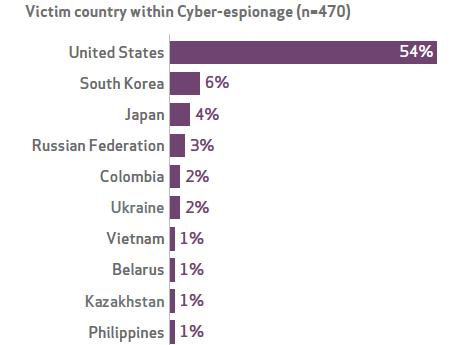
But public agencies were targeted more often than any business sector included in the report, and the United States was the No. 1 government target, accounting for 54% of government espionage.
The potential for damage from these incidents is real. In 62% of espionage cases the breach went months before being detected, and in 5% it went on for years. In 85% of cases the espionage was discovered by an outside third party rather than the victim.
Figure 2: 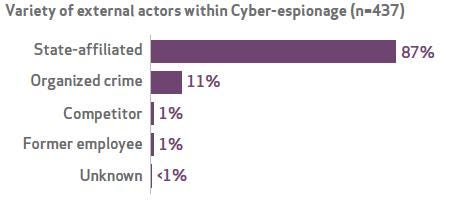
Figure 1: 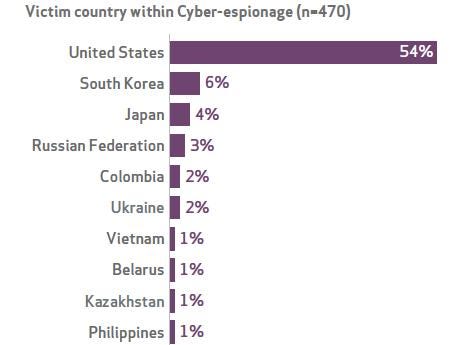 Source: Verizon 2014 Data Breach Investigations Report
Source: Verizon 2014 Data Breach Investigations Report
The Verizon report analyzed 63,437 security incidents from 2013 reported by 50 organizations in 95 countries. Government contributors to this year's report include US-CERT, the Secret Service, the Defense Security Service, the Homeland Security Department's National Cybersecurity and Integration Center, and the Commonwealth of Massachusetts, all in the United States, along with agencies from Argentina, Australia, Columbia, Denmark, the European Union, Ireland, Luxembourg, Malaysia, the Netherlands, Spain, and Ukraine.
Governments participate in the study because it anonymizes the incidents and provides high-quality data, says Sartin. "At the end of the day, it's not a survey, it's investigations of data breaches."
The surge in cyber espionage was surprising. "We knew it was pervasive, but it's a little disconcerting when it triples last year's already much-increased number," the report authors wrote.
Much of the increase reflects the growing number of participants in this year's report, they said. But espionage still could be underreported because there are few requirements for publicly reporting it, and the characteristics of attacks vary greatly, making them difficult to identify.
Identifying the source of the espionage also is "really, really hard," the authors said. Still, they think at least 87% of reported espionage is being done by nation states, and about half of it seems to be from
Eastern Asia. "Two countries in particular, the People's Republic of China and the Democratic People's Republic of Korea, represent that region," the report notes.
Attackers are using a diverse array of tools in espionage, but the most common is spear phishing. Email attachments are used to deliver 78% of identified espionage attacks, and links within emails deliver 2%.
Figure 3: 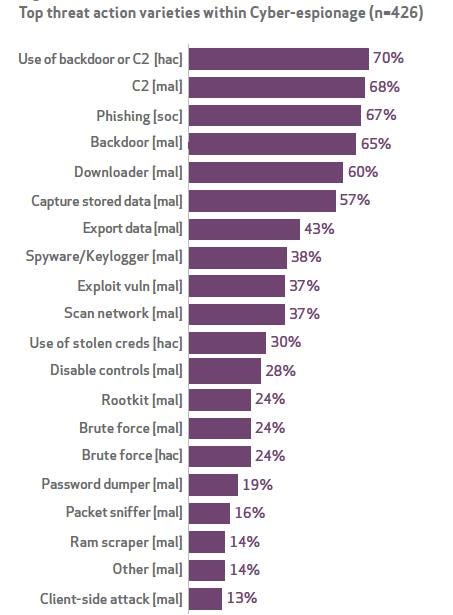 Source: Verizon 2014 Data Breach Investigations Report
Source: Verizon 2014 Data Breach Investigations Report
Because exploits used for espionage are varied, the recommended controls to counter them run the gamut of basic cyber security:
Patch everything.
Use updated antivirus.
Train users.
Segment your network.
Keep good logs.
Break the exploitation chain by detecting phishing attempts and interrupting them when someone "clicks."
Spot command and control traffic and data exfiltration.
Stop the lateral movement of attackers who gain access to the network.
The report also found the use of stolen and/or misused credentials (user names and passwords) continues to be the most frequent way attackers gain access to information, making the case again for using two-factor authentication. The report also noted that insider attacks are on the rise, especially for intellectual property.
Our InformationWeek Elite 100 issue -- our 26th ranking of technology innovators -- shines a spotlight on businesses that are succeeding because of their digital strategies. We take a close at look at the top five companies in this year's ranking and the eight winners of our Business Innovation awards, and offer 20 great ideas that you can use in your company. We also provide a ranked list of our Elite 100 innovators. Read our InformationWeek Elite 100 issue today.
About the Author(s)
You May Also Like







