Too many healthcare environments cling to insecure legacy systems and lax accessibility standards. It's time to enact strong security leadership.

Healthcare IT Cloud Safety: 5 Basics
Healthcare IT Cloud Safety: 5 Basics (Click image for larger view and slideshow.)
Facing potential HIPAA audits, some healthcare organizations are struggling to attain full-fledged security.
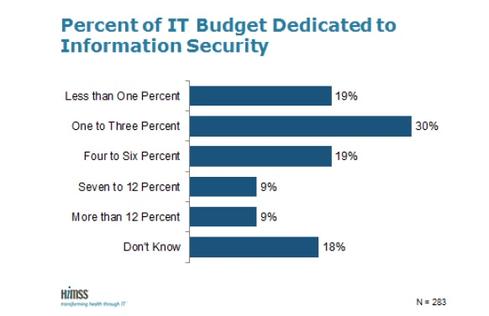
Until healthcare providers recognize and address their security weaknesses, they risk data loss, vulnerability to hacking, and HIPAA non-compliance. While some hospitals are expending the appropriate resources, experts say too many have yet to fully embrace the philosophy and culture of security necessary to protect patients, employees, and partners. Currently about 52% of healthcare organizations have a full-time resource for security, according to the 6th Annual HIMSS Security Survey. In terms of investment, 30% spent 1% to 3% of their budgets on IT security; 19% spent less than 1%, and another 19% spent between 4% and 6% of IT budget, the report found.
HIPAA mandates healthcare organizations designate someone to formally oversee HIPAA compliance. But that individual is not necessarily a chief security officer or chief information security officer, cautioned Brian Evans, senior managing consultant at IBM Security Services, in an interview. It could be a nurse, administrator, IT executive, or even combination of people who take on the role in addition to other responsibilities.
"I would say a majority [do], but I'd be hesitant to hedge on any kind of majority that may have someone who's designated," he said. "On paper they can say, 'We have somebody dedicated to the cause.' In reality they may have not have the skillsets. "
[Insecure communications in healthcare can be costly and dangerous. It's time to step it up. Read Insecure Communications Costly For Hospitals.]
Rather than hire a dedicated CSO, some healthcare providers implement security "by committee." "There is nothing in the HIPAA security rule that says you cannot [do that]," said Evans. "It's more challenging to manage a security program and function by committee. I would say we still have a long way to go for the level of security maturity we need within healthcare."
Finding a CSO, however, can be challenging. Many providers want a CSO with prior healthcare experience. One of Evans' clients, for example, received many contenders with excellent security credentials but no industry knowledge. The client ultimately hired a CSO with less security knowhow. "I advocated I could teach the healthcare experience much easier than I could teach them the security," Evans said. "Those candidates, quite frankly, were less qualified based on their security skills and experience -- but they had spent time in healthcare and that had been [the client's] true qualifier."
Physicians and other healthcare "end users" can be particular, and many are resistant to onerous security measures. But they are no different in that regard from other professionals, such as pilots, Evans pointed out. CSOs driven to help their new healthcare organization become more secure want to learn the terminology, workflow, and business processes, and they will do so in order to succeed.
Perhaps most importantly, CSOs bring order to the chaos of an unstructured, unmanaged approach to security. Without appropriate leadership or resources, hospitals cannot fully integrate security throughout the organization, conduct full risk assessments, or create a governance structure. Security processes must separate vulnerabilities and threats, Evans said, not lump them together. And healthcare organizations must follow stringent policies and methodologies.
Governance, risk, and compliance permeate every aspect of Health Care Service Corp. (HCSC), according to Ray Biondo, CISO of the insurance giant. "Every new technology we introduce, every old technology we retire, technologists have to follow. As a security organization -- we're more of a governance risk and compliance group -- we're the ones who make sure these processes are being followed," Biondo said in an interview earlier this year.
"We're also self-checking. We self-audit," he continued. "A lot of people don't understand what governance means. Governance means you're not only following the right controls put in place, but you have good solid oversight of how these processes are being followed. You're ensuring people are following processes you've put in place."
Without full-time security leadership, some hospitals can't correctly address even security basics such as encryption and passwords. Evans cited one example in which a hospital standardized on two-character passwords because legacy software could not handle more complex security measures. The better approach: Standardize on more complicated password procedures, such as a minimum of eight characters including numbers and symbols, and create an exception for the legacy application.
Of course, CIOs help protect hospitals, but their focus often centers on how technology can enhance operations in areas such as improving patient care, streamlining communications, or increasing bill collection. CSOs, however, address all areas of security, including physical safeguards and even old-fashioned media like paper.
"When we think of data breaches and security law, the first thing that comes to mind is someone hacking into a computer network or stealing a laptop -- but we all [still] have paper," Jennifer Christianson, a shareholder who specializes in healthcare law at Carlton Fields Jorden Burt, pointed out. "You have to think of physical security -- basic things like where printers are located, what kinds of computers you have, who has access internally at your company to sensitive information. People need to reexamine not just security for networks and computers, but physical security."
Cyber criminals wielding APTs have plenty of innovative techniques to evade network and endpoint defenses. It's scary stuff, and ignorance is definitely not bliss. How to fight back? Think security that's distributed, stratified, and adaptive. Get the Advanced Attacks Demand New Defenses report today. (Free registration required.)
About the Author(s)
You May Also Like







