Review: Six Rootkit Detectors Protect Your System
While many security suites have a basic level of detection, these standalone tools will do a search-and-destroy on the rootkits that may be hiding in your system.

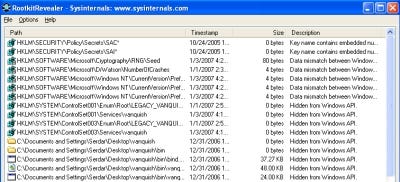
In October 2005, Windows expert Mark Russinovich broke the news about a truly underhanded copy-protection technology that had gone horribly wrong. Certain Sony Music CDs came with a program that silently loaded itself onto your PC when you inserted the disc into a CD-ROM drive. Extended Copy Protection (or XCP, as it was called) stymied attempts to rip the disc by injecting a rootkit into Windows — but had a nasty tendency to destabilize the computer it shoehorned itself into. It also wasn't completely invisible: Russinovich's own RootkitRevealer turned it up in short order. Before long, Sony had a whole omelette's worth of egg on its face, and the word rootkit had entered the vocabulary of millions of PC users.
The concept of the rootkit isn't a new one, and dates back to the days of Unix. An intruder could use a kit of common Unix tools, recompiled to allow an intruder to have administrative or root access without leaving traces behind. Rootkits, as we've come to know them today, are programs designed to conceal themselves from both the operating system and the user — usually by performing end-runs around common system APIs. It's possible for a legitimate program to do this, but the term rootkit typically applies to something that does so with hostile intent as a prelude toward stealing information, such as bank account numbers or passwords, or causing other kinds of havoc.
Many antivirus and security-software manufacturers have since added at least some rudimentary level of rootkit detection to their products, but there have been a number of free, standalone rootkit detection tools that have been in use for some time. In this article, I examine six of the more prevalent standalone applications, and talk about their relative merits and abilities. To test them out, I used them to scan a system for three varieties of rootkit: Fu or FuTo, which can "stealth" any process; the AFX Windows Rootkit 2003, which can hide processes and folders from the system; and Vanquish, which is similar to AFX but uses a slightly different concealment mechanism.
How They Work
The detectors themselves typically work by comparing different views of the system and seeing where there's a mismatch. One of the original ways to perform this kind of detection was to dump a complete list of all the files on the volume while inside the operating system, then boot to the Recovery Console and dump another file list, then compare the two. If a file shows up in the second list but not in the first and isn't a Windows file kept hidden by default, it's probably a culprit. More recent rootkit detectors use variations on this scheme that don't require exiting the operating system to get usable results.
I've also looked at these applications in a more general light and tried to consider how useful the program is likely to be in the future: how easy the detector is to use; how easy it is to interpret the results; how often the detector was updated; and so on. Remember that rootkits, like viruses, are a moving target. An anti-rootkit program that protects you today might be defenseless tomorrow against a whole new variety of threat — in fact, many rootkit makers write their programs to specifically avoid detection by some existing programs.
For the most part, these programs are for advanced- to expert-level users. They're not intended to be used as general-purpose solutions; they don't always distinguish between false positives (i.e., files hidden by the operating system deliberately) and real rootkits; they come with no warranty — they're provided "as-is" — and some of them (such as Trend Micro's product) have their core technologies available in a far more user-friendly version in a commercial product. In short, if you're not a professional, your best bet, at least for now, is to either hire a guru or use a mainstream product that has some kind of rootkit detection capability (such as Trend Micro Internet Security 2007).
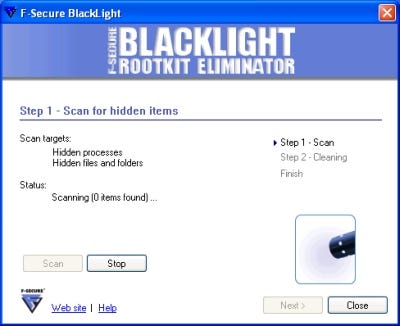
F-Secure BlackLight
F-Secure BlackLight was one of the first widely used rootkit scanners (aside from RootkitRevealer), and now that its scanning technology is being rolled into F-Secure Internet Security 2006, the current standalone version of the program may cease to be supported after April 1, 2007. Until then, though, it's still possible to download and use it. It's not clear if another version will be offered after that point, though, which makes BlackLight a way of enticing people to buy the more commercial implementation of the program.
|
BlackLight is strongly reminiscent of Trend Micro's RootkitBuster, not only in the sense that the core technology is part of another product, but in terms of its functionality. It's very straightforward: There are no settable options, just a pair of "Scan" and "Stop" buttons. On startup, BlackLight runs a pre-configured scan for both hidden files and hidden processes. But its detection system seems quite scrupulous — it caught a process hidden by the Fu rootkit and tracked down the other two rootkits.
The file system scan takes quite a while to execute, even on a relatively small system, and once it's done you can call up a list of all available processes that also have been detected. You're then given the option of cleaning any possible rootkits from the computer, which involves renaming the offending files rather than deleting them outright and forcing a reboot.
A minor annoyance with the wizard-like user interface is that you can't go back, only forward. If you make a mistake anywhere except on the current page, you have to start the whole program again.
One thing F-Secure has that few other rootkit detectors do is detailed documentation and usage instructions. Even if these programs are meant to be expert-level tools, it's always good to have something more to refer to than just the program's own prompts.
F-Secure BlackLight |
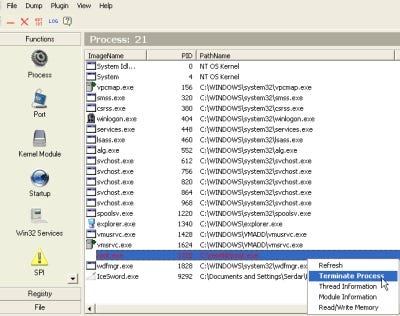
IceSword 1.20
IceSword has gained a measure of fame as being one of the most powerful and thorough rootkit detectors out there, although it's also one of the toughest to find. Its creator, a Chinese-speaking programmer known as pjf_, offers the program through his Web site, but since the link is excruciatingly slow the application has since been mirrored by many free download sites around the world (such as MajorGeeks.com).
|
The program itself was originally only available with Chinese-language prompts, but since then it has been issued in an English-language edition (although the help files for the program are still only in Chinese). Despite the language and availability barriers, I was able to get a copy without too much trouble, and the translated version of the program is quite legible.
IceSword performs a number of different system scans and attempts to determine if any hidden processes are influencing the results — running processes, startup programs, services, etc. There's also an all-in-one "System Check" screen, although it's inexplicably buried at the very bottom of the list of available scans and invisible by default. But if you run it, it will generate a fairly condensed report of any suspicious activity.
From there you can go to one of the more detailed reports, pull additional information about the offending process or file, and kill it off. It's up to you to perform any more sophisticated cleaning after that, though. I had a couple of minor stability issues with the program in its 1.3 edition: when I scanned for the AFX 2005 rootkit, for instance, the program crashed.
There's a number of small but elegant touches throughout, aimed at the experts that the program is intended for. The "Reboot and Monitor" function restarts the computer and then tracks any attempts to hide processes or Registry entries at boot time. "Forbid all process/thread creating" lets you "lock" the rest of the system from starting any new processes after IceSword has been loaded as a defensive measure. By default, you can let IceSword log the creation of new processes and threads, and analyze them for possible culprits.
IceSword also has been updated pretty consistently — multiple 1.x editions have appeared throughout 2006 — and pjf_ has been quoted as saying that he will continue to update and offer new versions of the program as different rootkits emerge. There's also a plug-in architecture that can be used to expand the program, although as far as I can tell there's currently only one add-on for it, which is used for low-level disk editing.
IceSword 1.20 |
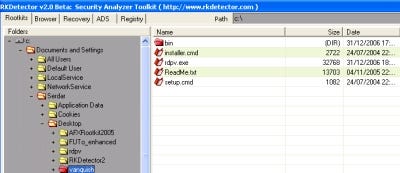
RKDetector 2.0
RKDetector is actually two applications — one to scan for hidden files on a hard drive, and another to scan for hidden processes and kernel hooks. It's a little more difficult to do a comprehensive scan this way, though — you have to do each scan action separately and there's no way to get a comprehensive report. The individual result reports aren't hard to make sense of and act on, but the program's usefulness is overshadowed by some of the other applications discussed here.
|
The main program sports five tabs — Rootkits, Browser, Recovery, ADS (for scanning NTFS alternate data streams, where rootkits also can hide), and Registry.
Before you scan with any of these, though, you have to provide a root path to begin the scan from (i.e., C:\); you can't just click-and-go. The Rootkits scanner tab is the best place to start and usually turns up the most results. Any directories that have concealed files will be marked in red; if they're concealed and not believed to be concealed legitimately by the operating system, they'll be marked heavily in red. One drawback to this approach that if you have a rootkit buried several directories down, you have to drill down to it manually, which is a little irritating.
Once you find the offending file, you can do a number of things with it: perform a hex dump on the file itself or the file's MFT table entry, save it as something else, or securely erase it (and the MFT entry along with it). The program uses the U.S. DoD 5200.28-STD secure-erase algorithm to insure that an erased file is erased, so use it with care.
I wasn't as impressed with the hook-analyzer / hidden-process detector portion of RKDetector — it didn't find any of the in-memory processes concealed by Fu, for instance.
RKDetector 2.0 |
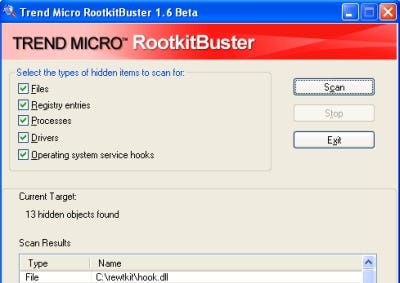
Trend Micro RootkitBuster 1.6
One of the things I've always liked about Trend Micro is how they make bits of their commercial products available as freebies. If you've been smacked with a virus, you can use their online antivirus engine to do a scan-and-clean. The same goes for rootkits: Trend Micro has excerpted the rootkit-detection technology from its commercial Internet Security 2007 product and made it available as a standalone tool. Documentation is essentially nonexistent and it's very hard to tell how regularly the product has been updated, but I suspect that goes hand-in-hand with it being a freebie.
|
Simple as it is, RootkitBuster actually doesn't do a bad job. The program runs as-is (no installation needed) and scans five areas: file system, Registry, running processes, drivers, and any operating system-level service hooks. The results are automatically exported to a log file, and if anything's detected you can opt to have it deleted (with a forced reboot afterward to insure deletion).
For some reason, RootkitBuster doesn't scan the service-hooks list by default, but the option to control this is presented to the user in the program's one-and-only interface, so it's not a big deal. (I suspect this was done to cut down on the amount of scanning time, since most rootkits will manifest in one of the other four categories anyway.)
The application also scans a bit faster than some of the others here, but the amount of information about the detected problems is skimpy compared with, say, what IceSword or Rootkit Unhooker provides. RootkitBuster does do a good job of detecting and cleaning, though — it caught processes hidden by the Fu rootkit, and found the other two test rootkits quite completely. All three were cleaned up nicely by the program with little more than a click of a button and a restart. It's not clear if RootkitBuster has measures to defend itself against subversion by a rootkit that's aware of it, however.
Trend Micro RootkitBuster 1.6 |
RootkitRevealer 1.71
RootkitRevealer (RKR) was one of the very first rootkit detection tools, courtesy of the ever-overachieving Mark Russinovich and Bryce Cogswell of Winternals (now part of Microsoft). It's fairly limited in scope, although it's been updated pretty regularly — the most recent version was published in November 2006 — and since Messrs. Russinovich and Cogswell are among the technical authorities on Windows out there, I would imagine it will continue to be updated, at least provisionally.
|
RKR is pretty simple to use. Fire it up (no installation required), click "Scan," and it will iterate through the Registry and the file system to try and find anything that's attempting to conceal itself from the operating system. The program does turn up a few false-alarm readings by default, mostly in the Security section of the Registry, but these are well-documented and easily ignored.
The results are displayed in an exportable report, but it's not possible to take action against any of the detected items in the program itself — you can't, for instance, right-click on a suspected file and mark it for deletion. Any action you take, you have to do so entirely on your own, which can be a little difficult if you're dealing with a cloaked file or process.
RKR's documentation indicates that it's not designed to detect rootkits that cloak themselves in memory only, such as Fu (which it didn't detect at all). It checks specifically to see if something is attempting to conceal itself in the file system or Registry, so in that respect it's limited.
It did detect signs of the other two rootkits, though, so as a quick-and-dirty first line of defense it's not bad. But for more comprehensive scanning and the ability to take more definitive action against a rootkit, there are definitely better tools available.
RootkitRevealer 1.71 |
Rootkit Unhooker 3.0
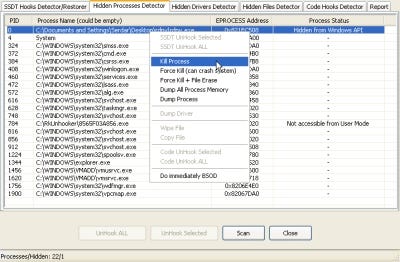
Like IceSword, Rootkit Unhooker may have unlikely origins — it's the product of a programming team from Russia — but it's one of the better and more comprehensive programs I looked at. That means it's also that much more sophisticated, but the programmers have been thoughtful enough to make it possible to produce an overview of all the scanned areas of the system in a single report.
|
When run, the program conducts an integrity self-test to insure that it's not being subverted by a rootkit that's aware of it. It trapped at least one of the test rootkits using this technique; when I went on to do the full system scan, Rootkit Unhooker gave me far greater detail about the rootkit and allowed me to cleanly terminate it.
Rootkit Unhooker is broken into six tabbed sections: kernel hooks, hidden processes, hidden drivers, hidden files, code hooks, and an overall report tab. You can click "Scan" in each one of the tabs to conduct a scan in that particular category, or you can go to the overall report tab and scan everything at once — a process which may take some time, as the biggest holdup is in scanning all available volumes in the file system. The full report is a bit wordy, but makes it unambiguously clear if there's a chance you've got a rootkit hiding somewhere — and where it might be hiding as well. I was able to detect the presence of all three test rootkits without trouble.
If you find an offending or suspect process, you can do a number of things with it: terminate it normally (i.e., as if it was an ordinary program being asked to close), force the process to close (which can, in theory, cause a crash), erase the file, or some combination thereof. If you kill and erase one or more suspect files, you should probably reboot and follow up manually with another scan to make sure the problem is gone. You can even force a BSOD — a last-ditch way to get things to stop running, short of pulling the plug. The single most intriguing feature is the "Virtual Machine Detector," which uses the time elapsed between two low-level CPU instructions to determine if the operating system is running directly on the PC or in a virtual machine. (At least one theoretical rootkit design involves "wrapping" the victim operating system in a virtual machine.)
Rootkit Unhooker has been updated pretty religiously — five times since November 2006 — and although some of its prompts are awkwardly translated into English, the language difficulty never obscures the program's functionality or usefulness. The coherency of the help file leaves something to be desired, though.
Rootkit Unhooker 3.0A |
Conclusions
The rootkit detection tools out there right now seem to break down into two basic categories:
Professionally written tools, which seem to be mostly marketed as a way to get people to buy a full commercial product.
Independently authored tools of broadly varying pedigrees and usability.
Ironically enough, it was one of the independent tools — Rootkit Unhooker — that turned out to be the best. I'm not sure that means the big vendors will see them as competition, though, since the indie-written tools clearly are meant for self-appointed pros.
If rootkits continue to proliferate and become as difficult to detect as is predicted to happen, that will be yet another selling point for the major security-software makers to market their own products. But it also will be an incentive for the indies to continue to write and update their tools for their own market, too.
About the Author(s)
You May Also Like