How Can CISOs Respond to 2019 Threats and Improve ROI?
Hint: It's continuous and automated.

As observed in ransomware hold-ups, credential-stealing malware and sophisticated Advanced Persistent Threat (APT) campaigns, 2019 has seen malware evolving around three main trends:
Evasion-by-design – Malware strains increasingly use file obfuscation and encrypted communications to evade AVs and endpoint security controls, respectively.
Living-off the land (LOTL) – A rising number of variants exploit legitimate system tools, enabling malware to run completely from memory (RAM).
Jack-in-the-Box – Underground botnet-as-a-service offerings enable cybercriminals to repeatedly push out new malware to already-infected systems.
How do you measure security effectiveness?
For IT and security managers, beefing up security typically means buying more security products. But before CIOs and CISOs go out and buy new products, they would be well advised to find out how effective their current security controls are.
And how do they uncover that? The same way you would check the safety of a car. Put it through a crash test.
When it comes to cyber security, crash-testing your controls with simulated cyber attacks lets you challenge, measure and optimize their effectiveness, without jeopardizing your production environment.
For example, would your web application firewall (WAF) block arbitrary command injections leading to a CapitalOne-style breach? Could your email and endpoint detection and response (EDR) foil a payload containing the latest flavors or ransomware? And if attackers attempt to exfiltrate sensitive data via steganography — hiding it in within other content formats such as images — would your data loss prevention (DLP) approach catch them red-handed?
This kind of testing can be performed using a variety of tools, including manual open source ones (e.g. End Game Red Team Automation, MITRE Caldera and others) and their more comprehensive counterparts, called breach and attack simulation tools, or BAS.
Continuous, automated security testing, in this context, enables organizations to enhance their detection capabilities by checking how currently deployed frameworks and configurations perform in the face of the latest techniques, tactics and procedures (TTPs).
Continuous testing against continuous threats
Reflecting a shift from binary, point-in-time decision-making to a more continuous and adaptive approach to the application of security controls (see Gartner’s CARTA model), continuous security posture assessments are gaining traction, complementing traditional periodic testing methods such as manual pen tests, red teaming and vulnerability scanning.
With continuous security effectiveness testing, security teams can address:
Daily surfacing of new threats – Ensuring their controls can detect the very latest threats’ indicators of compromise (IoCs) on an ongoing basis, enables teams to fine tune their defenses against them faster.
Advanced stealth techniques – To defend against fileless and signature less attacks, testing the effectiveness of behavior-based detection tools, such as UEBA, EDRs and deception honeypots is critical.
Frequent IT environ changes – Automated testing means you can preempt any adverse impact of ongoing IT alterations, such as configuration changes, software updates and new technology.
Limited resources and staffing – Security teams can continually tackle security gaps according to where their cyber risk is highest. By improving upstream security, fewer alerts are generated downstream for incident response.
State-sponsored threat actors – Organizations can continually test their ability to cope with techniques that APT groups are known to use, thus optimizing their defensibility against these attacks.
Supply chain attacks – Also called island hopping or long-lining, challenging controls that secure touchpoints with partners, including portals, email and web gateways, and endpoint controls, enables minimizing the associated risk.
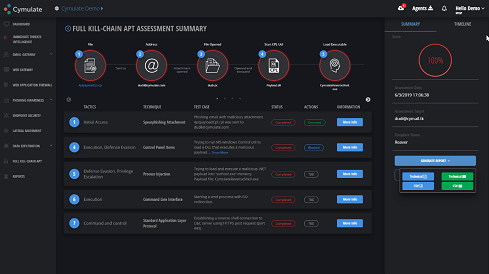
Continuous testing against APT groups’ TTPs enables defense optimization. (Click the image to see the full-size screenshot).
'Show me the money' - How ongoing testing improves security ROI
According to Bob Parsons, founder of GoDaddy, “Anything that is measured and watched, improves.” Until just a few years ago, when it came to measuring the cost effectiveness of security investments, your guess was as good as anyone else’s. Thanks to automated security testing tools, that information is no longer a speculation.
Utilizing industry-recognized standards such as the NIST Risk Management Framework, MITRE ATT&CK, Common Vulnerability Scoring System (CVSS) and Microsoft DREAD, security vendors have started to provide quantifiable metrics that enable leaders to make data-driven decisions, and have data-informed conversations with management and their teams.
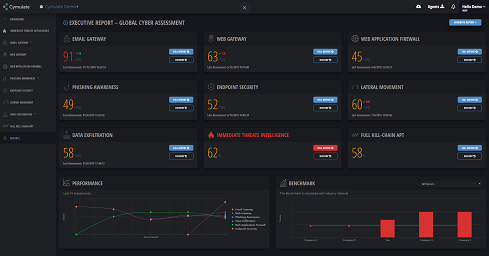
Objective KPI metrics enable increasing cyber security ROI.
How does it work? By crash-testing your security controls, you gain assessment results that include objective, quantifiable exposure scores as well as mitigation guidelines. These insights can be used to:
Prioritize remediation – Invest time and effort strategically, starting from where threat exposure is highest.
Hold BAS bakeoffs – Purchase decisions can be made according to how well comparable technology performs in the face of attack simulations.
Demonstrate security performance over time – How have your investment decisions improved security scores? Were visible dips a result of cutbacks or turnover?
Benchmark against industry peers – Compared to your industry, is your security posture in good shape? Per attack vector (email, endpoint, etc.) do you fare better or worse than your competitors?
Reduce dependence on pen tests – By continually testing controls, you can engage external pen testers for compliance and specific exercises, rather than relying on them to uncover your blind spots.
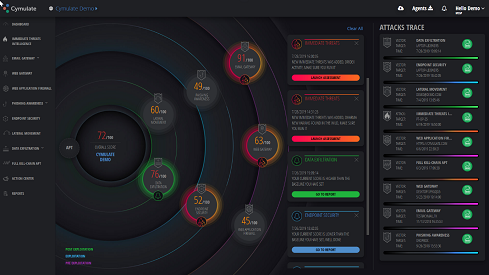
Cyber exposure scores enable assessing security control effectiveness.
To learn why organizations are moving to continuous security effectiveness testing, get your complimentary copy of Gartner’s report, titled How to Respond to the 2019 Threat Landscape.
Ready to explore automated security risk assessments? Sign up for a free trial here.

About the Author
You May Also Like






