What is Zero-Trust Data Management?
Legacy backup solutions are good at recovering from natural disasters and IT failures; ransomware recovery requires you to rethink your security strategy. Learn why you need zero-trust data management. (Sponsored)
September 20, 2021

“The threat of severe ransomware attacks pose a clear and present danger to your organization.”
Such an ominous warning could be straight from the script of a high-budget action movie. Unfortunately, this is a real-world advisory from The United States Department of Justice in June 2021. Just days earlier, Christopher Krebs, the former head of the Department of Homeland Security's Cybersecurity and Infrastructure Security Agency, testified before Congress, that "we are on the cusp of a global pandemic of a different variety, driven by greed, an avoidably vulnerable digital ecosystem, and an ever-widening criminal enterprise."
A thriving ransomware economy has emerged. Ransomware hackers are getting smarter and now going straight for your backup data, so backup data must be inherently secure so attackers can’t hold data hostage. And while legacy backup solutions are good at recovering from natural disasters and IT failures, ransomware recovery requires you to rethink your security strategy. If data is the target, then security defenses must begin at the point of data.
The Need for Zero-Trust Data Management
Traditional IT security defenses are failing. The bad guys are breaching firewalls and bypassing endpoint protections. The breakdown of the perimeter is driving a zero-trust approach to cybersecurity. A zero-trust architecture assumes all users, devices and applications are untrustworthy and can be compromised. In other words, trust nothing, always verify. Only multi-factor authenticated users get access to data, permissions limited, and specifically their ability to maliciously impact data is removed.
So, what does a zero-trust architecture for data management look like? The need to adhere to the model defined by the National Institute of Standards (NIST), which is defined by the NIST SP 800-207 Zero Trust Architecture Specification. As NIST puts it, zero trust comprises “an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources.”
What is Zero-Trust Data Management?
Zero-trust data management is an architecture that is modeled after the zero-trust Implementation model from NIST. At the core of zero trust is the need for a system, which supports a purpose-built file system that never exposes backup data via open network protocols. This creates a logical airgap that blocks data from being discoverable or accessible over the network.
Once data is written to the system, it cannot be modified, deleted, or encrypted by an attack, ensuring that a clean copy of data is always available for recovery. Multiple expert-guided recovery options, including Live Mount, Mass Recovery and AppFlows orchestrated recovery, are built-in so IT teams can quickly recover the files and workloads impacted by an attack.
What Zero-Trust Data Management Means For:
IT teams can now protect critical data from ransomware attacks, giving their organization the ability to recover data and applications quickly without paying a ransom
Security teams can now confidently leverage secured backup data to perform attack forensics, and initiate recovery operations directly from their security operations center
Application owners can now rest easy knowing that business data is protected, and that if a ransomware attack were to occur, applications can be restored quickly to maintain business continuity
CIOs and CFOs can now be assured that ransomware recovery plans are supported by a zero-trust architecture that enables the organization to minimize cyber insurance costs and prevent reputational damage resulting from ransomware attacks
Zero-trust data management goes to the heart of data protection -- keeping hackers out of your backup system, identifying ransomware activity, and making sure all data has a clean backup that can be recovered quickly.
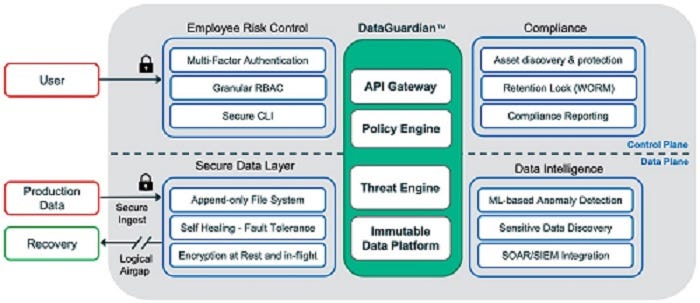
We start with some core pieces that are foundational to zero-trust data management.
Reduce the risk of intrusion – all system interfaces are secure, role-based, least privileged, and protected by 2FA -- trust nobody and no system
Secure the data – data is always encrypted in-flight and at rest, and backup data is stored in a purpose-built append-only file system. Backed up data is always logically air-gapped so it’s offline and not accessible through standard network protocols
Detect and alert anomalous behavior – detect an attack, alert the SecOps team, and pinpoint a clean recovery point
Enforce compliance – automatically protect new workloads, lock retention, and find certain exposed sensitive data that may have been exfiltrated
The message from the highest levels of government and security experts is clear: The bad guys are getting through traditional security defenses -- and they are targeting your backup data as a growth strategy. It is time to rethink your data protection strategy, to set up new backup and recovery requirements based on zero-trust principles, and to make IT investments that secure your data to help ensure your organization never has to pay a ransom.
Need help building your ransomware recovery plan? With Rubrik’s Zero Trust Data Management™, you can protect your data and applications from ransomware, natural disasters, and operational failures. Learn more at rubrik.com/ransomware

Dan Rogers is President at Rubrik, where he brings over 20 years of product and marketing experience. He has held leadership positions at AWS, Salesforce, Microsoft, and most recently, served as the Chief Marketing Officer at ServiceNow.
You May Also Like




