Shadow IT: Honey Badger Better Care
Use of Dropbox and other consumer services is exploding in enterprises, yet companies turn a blind eye to the security risks. This sends the wrong message to cloud service providers.
Late last week, popular SaaS storage provider Dropbox admitted to a web vulnerability that put the confidentiality of data at risk. Its response was to shut off link-sharing functionality to prevent abuse -- a decision that was not, if comments on its blog post about the decision are representative, well-received. Not only did this vulnerability put users at risk, its remediation apparently disrupted workflows across enterprises and thus negatively affected a key business performance indicator: productivity.
According to SkyHigh Networks' Cloud Adoption Risk Report for the second quarter of 2014, Dropbox remains the No. 1 file-sharing service in use across more than 250 companies, spanning the financial services, healthcare, high tech, manufacturing, media, and services industries. Unfortunately, there's only one "enterprise-ready" cloud service as defined by Skyhigh Networks in the Top 10 file-sharing services list, and it ain't Dropbox. That honor belongs to Box, which comes in at No. 4 on list.
It's nearly a sure bet that you have users -- or entire departments -- blithely saving business data to Dropbox or some other file-sharing service. Unless you have complete control over every user's desktop (VDI vendors are right now salivating over this use case) it's highly unlikely that that "shadow IT" passed you by.
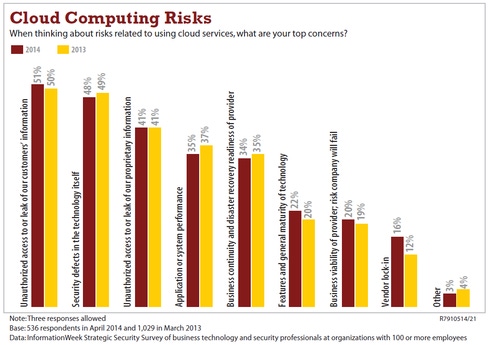
[How does distrust affect cloud businesses? Read Data Protection Fears Vs. US Cloud Market.]
Most CIOs readily acknowledge that, yes, unauthorized cloud services are in use within the corporate demesne. Most also underestimate just how pervasive they are, says Tal Klein, VP of strategy for Adallom, another player in this relatively new cloud service security market. "Executives usually estimate something like 30 cloud services, and we usually find around 300,” says Klein. “We've yet to see a company with more than 1,000 employees that had less than 200 'shadow IT' apps.”
That's a precarious situation that should have the business concerned. Yet it's often business leaders themselves giving at least tacit approval, which dampens any kind of urgency that might be felt by those well aware of the risks.
And, there's very little impetus for providers of these services to get enterprise ready. Of the 3,571 services assessed by SkyHigh, only 7% met the criteria to be considered "enterprise ready."
Surprised? Don't be. If the users "paying" the bills -- whether via expense account or serving up your data for mining -- don't care, why should the provider?
CIOs need to confront this issue now. Yes, shadow IT has gone on for years. But SkyHigh claims the average number of services in use by organizations has increased in the last quarter by 21%. The longer you turn a blind eye, the harder it's going to get.
Although IT is simply not going to shut down shadow IT at this point, you might still be able to put into place the minimum governance necessary to ensure that services are not incurring unnecessary risk.
The first step is discovery -- get a handle on just what services are in use and by whom. Find out by using logs or by simply talking to business units in a non-confrontational way. Then do some research to see which meet your definition of enterprise-ready and which do not. For the latter group, steer users toward services that are, in the opinion of IT, ready for use in their enterprises given all the various business, industry, and legal requirements. It might mean putting in place the controls required to shut down unauthorized services and offering a grace period for users to migrate to a more acceptable cloud service. Consider creating or augmenting an existing enterprise app store that includes links to vetted cloud services -- those that make your "enterprise ready" grade -- so users can easily access acceptable options.
No matter how you approach the problem, approach it. Approach it now. Because cloud service adoption is continuing to accelerate, and the Dropbox vulnerability is not going to be the last security issue we're going to see.
Private clouds are moving rapidly from concept to production. But some fears about expertise and integration still linger. Also in the Private Clouds Step Up issue of InformationWeek: The public cloud and the steam engine have more in common than you might think. (Free registration required.)
About the Author(s)
You May Also Like







