Cyber Attackers Target Small, Midsized Businesses
As large companies beef up security, attackers seek out weak links and use social tactics to hit smaller enterprises.
June 18, 2014
Government Data + Maps: 10 Great Examples
Government Data + Maps: 10 Great Examples (Click image for larger view and slideshow.)
Many small businesses, especially those plugged into the federal contracting chain, falsely assume that they are immune to cyber attack. But according to a recent report by Symantec, the number of phishing and other targeted attacks aimed at small and medium businesses rose sharply in 2013 and is on track to go up again this year.
Although last year saw many major data breaches, federal agencies' and large firms' improved security efforts have forced attackers to move down the supply chain to gain access to sensitive data, according to Bill Wright, Symantec's director of government affairs and global cyber security partnerships.
Speaking at a recent government cyber security briefing at the Armed Forces Communications Electronics Association he cited Symantec's 2014 Internet Security Threat Report, noting that targeted attacks on mid-sized firms (those with 251 to 2,500 employees) and small firms (those with 250 employees and fewer) rose by 61% in 2013 from 2012 levels. Attackers are targeting fewer individuals but they are choosing targets more carefully. The duration of attacks went up from four days to slightly more than eight days in a "low and slow" strategy designed to reduce the target's suspicion. This increased sophistication on the part of attackers, Wright added, also reflects greater awareness of phishing attacks by companies and individuals.
[Want to be ahead of the game? Read NIST Security Guidance Revision: Prepare Now.]
Sophisticated spear-phishing attacks also involve social engineering. He noted that attackers have shifted focus, now contacting administration staff instead of top corporate officers. For example, an executive assistant at one firm received an email with an attached invoice. The assistant did not open the file, but soon after was called by an individual purporting to be a company official asking for information in the invoice.
Top targets for spear phishing in 2013 were government agencies and manufacturing firms. Attacks on larger firms actually decreased during this time period, dropping to 39% of all attacks, compared to 50% in 2012. Attacks on smaller firms held steady at 31%, rising only slightly from 30% in 2012. But while the number of targeted attacks on smaller firms didn't change, the Symantec report noted that when combined with mid-sized firms, it represents a 61% increase over 2012. The report added that attacks on slightly larger firms -- those with 500 to 251 employees -- actually rose from 36% in 2012 to 41% in 2014.
A major reason for this shift to small- and mid-sized firms is that large companies, especially those with government sector business, such as defense and aerospace firms, have improved their IT defenses and security procedures, he said. Attackers seeking intellectual property and economic data have shifted to the smaller contractors and suppliers subcontracting under the larger firms.
A new trend that's hitting individuals and smaller companies is "ransomware" -- software that locks up a computer and forces the user to pay the criminals a fee to unlock it. A similar scam is "scareware," in which attackers pose as software security firms, warning users that their computer is compromised and prompting them to click to a malicious websites for repairs.
Ransomware originated outside of the US, and in its earliest manifestations victims received a message purporting to be from law enforcement, claiming that their computer contained illegal information. It would then be locked down until the victim paid up.
According to Symantec, ransomware attacks exploded in 2013, showing up first in Europe and then moving to the Middle East and South America. Criminals using ransomware show a preference for using online payment systems, Wright noted.
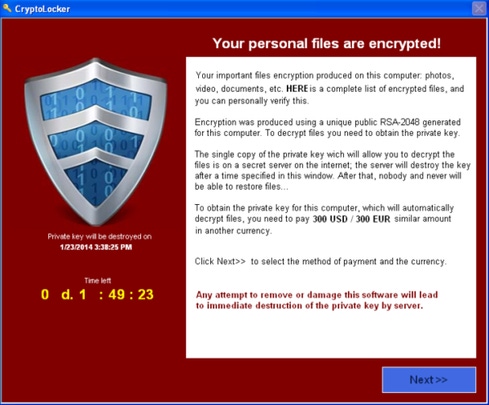
One proliferating ransomware script called CryptoLocker encrypts a user's hard drive and then threatens to wipe the drive unless a payment is made. The encryption software is very strong and extremely hard to break without access to sophisticated computing resources, he said. While CryptoLocker attacks are currently rare, he expects them to gain ground in 2014.
New standards, new security, new architectures. The Cloud First stars are finally aligning for government IT. Read the Cloud Hits Inflection Point issue of InformationWeek Government Tech Digest today.
You May Also Like





