Smartphones On Drones Can Hack Your Wireless Printer
Weak links in network security prove easy to find with drones and phones.

Drones: 10 Novel Uses For Your City
Drones: 10 Novel Uses For Your City (Click image for larger view and slideshow.)
People are often seen as the weak links in network security, but printers may offer another avenue of attack.
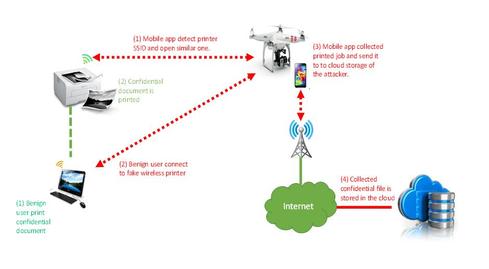
Researchers from iTrust, a cyber-security research center at Singapore University of Technology and Design, have used a drone carrying an Android smartphone to compromise a network through a connected WiFi-enabled printer.
Exploiting the erroneous assumption that printers can get by without wireless security, the researchers, including professor Yuval Elovici, Jinghui Toh, and Hatib Muhammad, created an Android app that can identify a printer's open wireless network. To get the phone with the attack app near enough to exploit the vulnerable printer, the researchers affixed the device to a drone.
The app was designed to hijack data. Print jobs sent to vulnerable printers ended up on the smartphone instead. The app then sent the captured files to the cloud via the smartphone's cellular connection and placed the files in the attacker's Dropbox folder. The app also has the ability to send captured print jobs back to the printer, in order not to arouse suspicion.
The use of a drone as a platform to attack networks may amplify concerns that drones need to be more tightly regulated. Worries about drones have prompted a backlash that threatens to slow their commercial deployment. On Tuesday the Federal Aviation Administration, still struggling to create rules to govern the use of drones, proposed a $1.9 million fine to punish drone startup SkyPan for allegedly conducting dozens of unauthorized flights over Chicago and New York.
That same day, California Governor Jerry Brown signed legislation to prevent paparazzi from flying drones over private property to take pictures. A drone "death ray" also debuted in Las Vegas this week at the Commercial Unmanned Aerial Vehicle (UAV) Expo.
[Read Facebook Drone Is Ready To Fly.]
But the attack vector needn't be airborne. The iTrust researchers also showed that their attack is feasible through a smartphone hidden in a robot vacuum cleaner. A smartphone running the attack software could just as easily be carried into a workplace, deliberately or unwittingly, by an employee, contractor, or visitor.
The researchers subsequently created a second app, called "Cybersecurity Patrol," to help IT managers mitigate this risk. Rather than hijacking print jobs, this app took a picture of the vulnerable printer and emailed it to the organization's CIO. It also sent remediation instructions to the printer.
Perhaps that's the future of vulnerability reporting.
About the Author(s)
You May Also Like







