40 BYOD Vendors, One Confusing Market
As enterprise IT gears up to battle mobility run amok, vendors are using a mix of acronyms to disguise few comprehensive offerings. Our research shows little distinction between products that are designated as BYOD and those that are MDM, MAM or something else altogether. So now what?

If there's one thing tech vendors hate it's being told that a marquee product is essentially the same as what competitors offer and, by the way, also not a great match for customer needs. But that's the reality today in the growing mobile device management market, as IT teams try to use software meant for managing mobile devices to secure the data on those systems. It's not all the MDM vendors' fault--mobile operating system vendors are either reluctant to share control of functions like encryption and policy enforcement (Apple), or they let device makers mess with the OS (Google) so they end up exposing the capabilities needed for MDM unevenly, if at all.
Mobile vendors care first and foremost about controlling the user experience--of prime importance in the battle for consumer mindshare. But that goal is fundamentally at odds with letting third-party software vendors provide all the features needed for enterprise-class security, as we discuss in our InformationWeek State of Mobile Security report. But instead of admitting that no one product can do it all, vendors often just slap new names on existing products, many times without adding a whit of new functionality, as they scramble for advantage in a hugely crowded market that is, frankly, overdue for consolidation.
To make sense of this market, we asked 40 vendors, from Absolute Software to Zenprise, not just about features, cost, and functionality, but also how they classify their products: mobile device management, mobile application management (MAM), bring-your-own-device suites, all of the above, some of the above, or the ever-popular "other." While (the so broad as to be meaningless) BYOD was the No. 1 answer, multiple categorization is also quite popular.
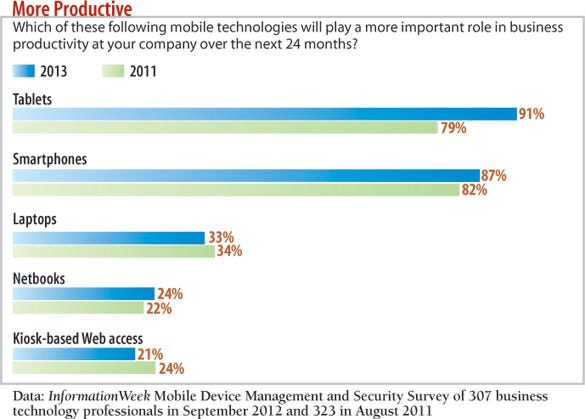
This is a bad time for confusion to reign. Ninety-one percent of companies think tablets will increase somewhat or significantly in importance, we find in our new InformationWeek 2013 Mobile Device Management and Security Survey. That's a 12-point jump from our August 2011 poll. Our survey also shows that 43% have MDM software deployed or are in the process of deploying it, compared with 39% still evaluating their options.
We understand IT's reticence to cut a purchase order. These suites tend to lack clarity in terms of not just what they're called, but what they can and can't do: 24 of the 40 vendors surveyed for this report say their offerings could be called a BYOD suite, but 14 also indicate that their BYOD products could qualify as some other type, including MAM and MDM.
Don't sit around waiting for vendors to put neat lines around these product categories. Your goal is to let employees be productive on their personal smartphones and tablets while maintaining data security, and that will likely take more than one software suite--at least until the next wave of ARM chips that support virtualization and allow for multiple personalities on phones: one work, one personal.
Good Technology
Classification: MDM and MAM Cost: Good Dynamics, $129 for unlimited apps on one device Deployment options: On premises Platforms supported: Android, iOS, Windows
"There is no such thing as a 'BYOD solution,'" says Philippe Winthrop, founder of the Enterprise Mobility Foundation, a community devoted to promoting the value of mobility. "Vendors are marketing to the pain points that end user organizations are dealing with. They are making the most of the buzz surrounding BYOD."
It's clear vendors are repurposing and renaming existing products with a BYOD tagline. The key for IT is to stay focused on the capabilities they need and what platforms they'll support.
"We are currently in the trial/testing stages of two MDM vendor software suites," says one survey respondent whose business has tied deploying MDM to a BYOD program. His company's biggest concern is wiping all corporate data from the device in the event it's lost or stolen or the employee leaves the company. You'd think that ability would be table stakes, but only 22 of our 40 vendors offer remote wipe. That's just not good enough--remote wipe came in at No. 4 in desirability among 18 features for centrally controlling mobile devices in our survey, behind only compliance and policy creation and enforcement and the ability to push out updates. In addition, the company plans to enforce strong security measures on the devices, such as passcodes, auto lock on idle, and no jailbroken or rooted devices. But nine vendors don't give IT the ability to take action--such as preventing a device from accessing the network--if that device is not in compliance with those kinds of security policies. (You can download vendor responses here.)
The boxes below and on the previous page show how even established vendors like Good and Symantec are slinging acronyms; this phenomenon isn't limited to upstarts. So when issuing an RFP, understand, but don't be limited by, the distinguishing characteristics among the major categories of products on the market that address BYOD.
MAM: Mobile application management systems enable IT to manage apps on mobile devices. This includes pushing software packages and related configuration files onto devices, maintaining an inventory of installed software and versions, and updating software when new versions come out. MAM can also enforce application blacklist and whitelist rules about software allowed on devices and present a catalog of both available and recommended applications to employees. Companies that specialize solely in MAM include AppCentral (although its offering is extremely limited), FeedHenry, Kony, Mocana, and Partnerpedia.
MDM: Mobile device management encompasses products that manage the devices themselves, as if they were any other element in the network. MDM systems complete a number of jobs, including enrolling, provisioning, tracking, maintenance, and backup, but the term is fast falling out of favor. Among our 40 vendors, only Wyse calls itself pure-play MDM. That doesn't mean it lacks security-focused features; in fact, Wyse checked most boxes. So again, don't go solely by acronym.
We also asked about WLAN access management functions focused on protecting corporate Wi-Fi networks when employees connect personal devices. These systems also measure network performance and uptime, provide tools to address problems, and can detect when devices or rogue access points are added. Fluke Networks is the only respondent company that focuses solely on WLAN access management.
Symantec
Classification: MDM and BYOD Cost: $72 per user Deployment options: SaaS, on premises, virtual appliance Platforms supported: Android, Blackberry, iOS
As for the six vendors that say their suites do "everything," our research indicates otherwise--five lack at least one element: Absolute Software has no call blocking or call routing; Antenna Software lacks file/folder-level encryption and call routing; BoxTone has no call blocking or call routing; Fiberlink lacks call routing; IBM can't prevent malicious app downloads, block mobile malware, or provide call routing. AirWatch is the only one that checked every box.
"There are many products that label themselves MDM that do both MDM and MAM and even a few more things, like anti-malware or VPN," says Lisa Phifer, president of consultancy Core Competence and a specialist in mobile device security. "This creates confusion in the marketplace as MAM vendors try to pigeonhole MDM products into just device management."
Unfortunately, you may need to budget to overlap a few products until some acquisitions happen and leaders emerge. That likely won't occur for at least 18 months, says Winthrop. The good news is that most vendors offer a mix of software-as-a-service, on-premises software, and physical and virtual appliances. We present pricing in our report, with a range from $10,000 to even get started to $4 per device per month in a SaaS offering. Winthrop says it's also possible that enterprises will decide BYOD is not the best approach. "Instead, there are companies taking a corporate-owned, personally enabled--COPE--mentality, in which the enterprise purchases a device and service plan that the employee wants," he says. We suspect few IT pros will mourn the passing of BYOD.
Denise Culver is a technology journalist. Write to us at [email protected].

InformationWeek: Oct. 11, 2010 Issue
Download a free PDF of InformationWeek magazine
(registration required)
About the Author
You May Also Like






