Mobile Device Management On The Edge
Our survey shows we're moving at a breakneck pace toward pervasive mobility. Here's how to stay safe.

Moving from Lotus Notes to Google Apps propelled one global nonprofit organization head-on into the law of unintended consequences. "It has caused an explosion of users bringing their own devices for accessing their work email," says the project's manager. "Most to all MDM solutions rely on some type of ActiveSync connection to manage devices. In our Google Apps environment, with IMAP services open--a business requirement--and without a single-sign-on policy and system in place, we're unable to control who has access to their work email on personal mobile devices."
The organization is now evaluating several mobile device management (MDM) systems. Problem is, in order for this shop and others like it to regain control, Google must expose an API to take the place of ActiveSync, and Google won't confirm when, or even if, it will make this API available.
Welcome to the wild new world of mobile device management.
If you're a glass-half-full kind of person, you may see improvements in the manageability of consumer-class mobile devices as coming just in time to offset battered budgets. But any savings realized by letting employees use their own phones for business can be wiped out if just one Droid containing customer information is lost and you can't nuke it remotely. And that's not a given with MDM products, whose capabilities vary widely, as we'll discuss.
The 323 respondents to our August Mobile Device Management and Security Survey, all of whom are involved with their organizations' mobility strategies, are running into other problems, too. The IT director for a multibillion-dollar U.S. construction firm is using ActiveSync to manage smartphones as he waits for management to pull the trigger on a new strategy. "Only phones that can be encrypted, PIN'd, and wiped by us are currently allowed," he says. The company plans to move to a personal-liability model, where employees buy their own wireless devices and services and may be reimbursed for some or all expenses, and expand the variety of phones and tablets that can access the network. To that end, IT is piloting Good's Enterprise for security, while also crunching numbers for expense reporting vs. stipends. "Good creates a container that holds all interactions with the company network," he says. "We feel that addresses security. Now the sticking point is reimbursement."
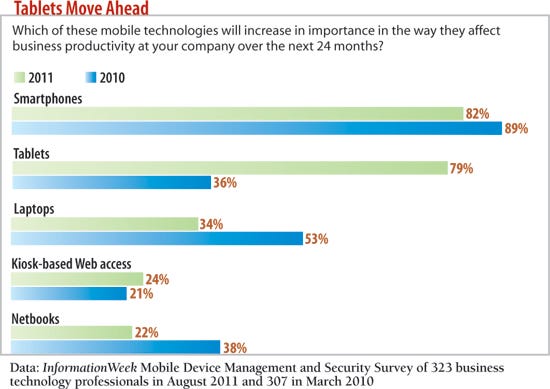
There are a lot of moving parts, and the "bring your own device" movement is gaining momentum, with 65% of our survey respondents predicting an increase in the number of employee-owned smartphones and tablets accessing business data and networks. It's time to develop a policy describing how mobile devices are to be provisioned, managed, secured, and disposed of, and to put in place technology enabling IT to enforce that policy.
Remember, the name of this game is managing the component pieces--email profiles, on-premises and software-as-a-service applications--in a way that makes it easy for people to work while also giving you the confidence to look an auditor in the eye and say you're comfortable with the potential loss of any device. If you can't do that, you have a problem.
We're also in the midst of huge platform shift. How huge? As of July, Google Android owned almost 42% of the 82.2 million-user U.S. smartphone market, up from 36% in April, according to ComScore. Its gains come mainly at the expense of RIM's BlackBerry, which was at 22% in July, down from 26% in April. Apple's iPhone market share was at about 27%, with Windows limping along at around 6%.
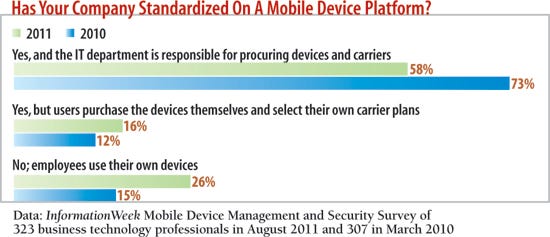
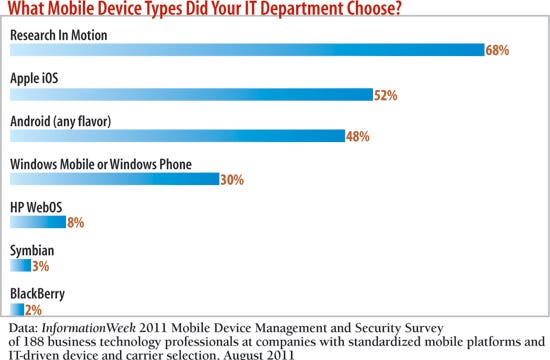
Now compare those percentages with the fact that, among respondent organizations with standardized mobile platforms dictated by the company, 68% use BlackBerrys. If IT were still running the show, Research In Motion's market share numbers would be a lot healthier, its recent network outages notwithstanding. That's because consumer devices scare the heck out of many IT pros, who assume they aren't "enterprise-ready." For example, we asked in our survey whether each platform provides effective authentication, encryption, and management controls. BlackBerry, cited by 74%, is the undisputed poster child for "enterprise class."
Mobile Device Management Our full report on mobile device management is free with registration. This report includes 41 pages of action-oriented analysis packed with 32 charts. What you'll find:
Our full report on mobile device management is free with registration. This report includes 41 pages of action-oriented analysis packed with 32 charts. What you'll find:
Reader usage ratings of 21 MDM vendors
Platforms supported for mobile application development
But IT isn't running the show, and RIM isn't the only game in town for secure mobility. The data-protection mechanisms that are part of Apple's iOS, for example, support hardware-level cryptographic keys and a cohesive sandboxed application security architecture. Although iOS may not be ready for military-grade FIPS operation, the 22% of survey respondents who think it's not manageable and secure aren't paying attention.
Android, on the other hand, is all over the place on manageability and security, and for the most part it isn't up to par with BlackBerry and iOS. The 43% of survey respondents who rate Android 2.3 and older versions as not ready for business are right on. The versions before Honeycomb (pre-3.X) have little to no built-in security.
Erich Stuntebeck, a researcher for MDM vendor AirWatch, says Droid vendors such as Motorola, HTC, Samsung, and LG are now forced to write security APIs for their versions of the OS since the "enterprise desired" functions aren't native. And to make matters worse, just because a device is running Honeycomb, which has security capabilities, doesn't mean the phone manufacturer has leveraged those capabilities for a given model.
The MDM vendors we spoke with say Google is beginning to take enterprise readiness more seriously as it develops new versions of Android. It's working to embed functionality such as encryption and support for Exchange within the core of the OS, in lieu of relying on multiple vendor-specific APIs. And in October, a company called 3LM announced standardized security extensions embedded within the native Android OS. CEO and co-founder Tom Moss says 3LM, owned by Motorola Mobility and including former Google execs, aims to catalyze enterprise adoption of Android by patching the main versions of the core OS from each of the major manufacturers. It will do this with a set of hooks that can be used by MDM systems to alter and influence about 60 security policy settings.
Interestingly, 3LM's software has been part of the main Android development efforts since June, but Google hasn't turned it on until recently. Several top-tier device and management vendors, including AirWatch, BoxTone, MobileIron, and Motorola, plan to support the standardized 3LM Android control hooks. We'll be interested in how enterprises leverage this standardization and whether major device manufacturers continue to write management APIs or instead rely on the libraries developed by 3LM--which is poised to be absorbed into Google via its Motorola Mobility acquisition.
Windows Phone, meantime, needs time to mature. It doesn't yet have the built-in OS facilities to be considered enterprise-ready--the current release lacks an encrypted file system, complex-password capabilities, and VPN connectivity. But Microsoft isn't standing still, and you can bet that upcoming releases, including Mango, will begin to address these shortcomings.
Security's Job 1
Our survey data shows an uptick in the number of respondents placing mobile data security among their top priorities. But we worry that many are taking a tactical approach--comparing a few MDM suites, buying one, then jumping right in and configuring lock-down policies willy-nilly, inciting an employee revolt.
If that sounds like you, take a deep breath, step back, and approach this issue strategically. Define in writing how your mobility strategy will work. Once you know what you want to accomplish (because you've done your homework), putting your plan into action using one or more security controls becomes much easier. Form a cross-functional mobility council comprising IT, lines of business, and a few users with heavy mobility needs. The diversity of ideas will serve you well.
Determine your level of risk based on the types of data you handle. Higher-risk data translates into stricter policies, no matter how much sales wants to carry the customer list on iPhones. Ask your short-listed MDM vendors to weigh in on each phase of your device life cycle--from purchase to enrollment to operation to disposal. Define who pays for the device and data plan. Put the mobility policy in writing, and have users sign it. Only then is it time to put security and management controls in place.
Is ActiveSync Enough?
Microsoft Exchange ActiveSync (EAS) was developed to permit a variety of phone platforms to receive "direct pushed" email, scheduling, contacts, and tasks over secure SSL connections. When a user's account is enabled for ActiveSync--that is, supported mobile devices are permitted--the user can access her data. But while ActiveSync is the most common mobile device manager, it touches only the most basic of basic policy types, and these will vary by the version of ActiveSync your organization uses and the mobile devices it supports. With ActiveSync, administrators can set policies for remote device wiping; enforcing device passwords, minimum password length, and alphanumeric passwords; and setting inactivity time lockouts. That's about it.
In short, ActiveSync is much better than nothing. But today's level of mobile platform fragmentation, not to mention the lightning pace of hardware change, means really effective risk reduction and comprehensive management are just about impossible with EAS alone. For that, you need an enterprise-class mobile device management platform.
MDM Decision Points
So let's say you're ready to spend money on an MDM system. Which one do you buy? We outline some things to consider in our buyer's guide. Here are a few additional points to address:
>> How much is your company willing to spend per device per month? It's a competitive market, with new players entering the space, and MDM vendors are in a deal-cutting mood.
>> Do you want a software-as-a-service or on-premises system? For small organizations or those not ready to spend for redundancy, SaaS may be perfect. Don't discount this option.
>> Does the vendor use gateway servers to deliver secure communications, somewhat like the BlackBerry and Good architectures? If so, what role do these gateways play in ensuring security and compliance? Do the gateways integrate with company-developed applications to provide better security for them?
>> How many bells and whistles do you want? Is midlevel device management (a step above ActiveSync) good enough, or are you looking for that capability plus advanced device status and reporting features? Some MDM vendors label their products mobile systems managers, implying they control device security and provide lots of device metrics, such as calling time and data consumption. Don't be swayed--the MSM designation is mostly marketing.
>> Do you need controls for international travelers so that you're not getting stuck with $1,000 data bills?
>> Which vendors use device agents on which platforms? Some systems eschew agents and instead track mobile device status using the back-end infrastructure. Understand what modifications are needed to make this happen.
>> Do the MDM products you're considering support partial wiping? This capability is very important for organizations that permit BYOD.
>> Do you want to remotely control devices or back up data?
>> Are you looking for geolocation tracking or other functions based on location? For example, the CFO's phone turned up in the hinterlands of Asia. Maybe you should wipe it completely even though she owns it. Or maybe you want to automatically disable cameras on all phones that come within 300 feet of your company's buildings worldwide to prevent data theft via the camera.
Focus also on granular manageability. Different mobile platforms, and even individual versions therein, will always offer different and ever-changing levels of security. Your MDM vendor must be willing and able to consult with your IT team on the relative risk of allowing various iOS versions vs. Android 2.x vs. Android 3.x vs. Windows. IT shouldn't have to know the particulars of each individual platform--that's a full-time job in itself. Ideally, the MDM system will abstract this complexity, implementing controls under the hood. Directory integration is also vital. Whenever possible, the mobile policy pushed to a user's device should be tied to membership in a directory-based group, such as in Microsoft Active Directory. If an employee quits and is removed from the central directory, a typical HR process, this action should initiate a partial wipe of enterprise data from the device. In addition, look for:
>> Self-service: IT teams already have too much on their plates. The ability to provision devices via self-service portals is a big plus. Or say a user steps over the bounds of a policy by installing a blacklisted app. The MDM system should notify the user of what he needs to do to bring his device back into compliance.
>> Scalability and failover: These considerations are particularly important if you're running your MDM system on-site as opposed to as a SaaS offering. On-premises MDM systems need to be servicing the communications that rely on them 24/7. Building in fault tolerance is expensive, but important.
>> Reporting: Insist on audit and compliance reporting as well as usage analytics and inventories.
Finally, because the trend is toward personally owned devices, if an MDM system can't differentiate between enterprise data and personal data, don't buy it. What happens if you wipe a smartphone owned by a former employee and he doesn't have a backup of his contact lists? Are you liable for the loss? Ensure that the MDM product lets IT remove enterprise digital certificates, email and VPN profiles, enterprise-specific apps, and other corporate data while leaving pictures of the user's Cancun getaway intact.
MDM systems can help you manage multiple mobile device platforms before the problem spins further out of control--and results in a career-halting data breach. But before you buy any self-proclaimed miracle cure, commit time and resources to defining how you envision these devices interacting with your data. Control is the hallmark of a successful mobile device management program. As you develop policies, your end goal should be certainty that all data and connectivity profiles--VPN or Wi-Fi--that provide entree to corporate networks are completely secure, even when your company is on the bat-out-of-hell track to full mobility.
Grant Moerschel is a co-founder of WaveGard, a vendor-neutral technology consulting firm.
Go to the sidebar:
Lessons From Our MDM Buyer's Guide
Visit our
Mobile Security Tech Center

InformationWeek: Nov. 7, 2011 Issue
Download a free PDF of InformationWeek magazine
(registration required)
About the Author
You May Also Like






