BYOD: Why Mobile Device Management Isn't Enough
Here's what to look for in MDM software and what limitations IT still faces in letting employees use personal devices for work.

Nine out of 10 technology pros think smartphones and tablets will become more important to business productivity in the next couple of years. Seventy-two percent expect to offer more bring-your-own-device options so that employees can access company data with their personal gadgets.
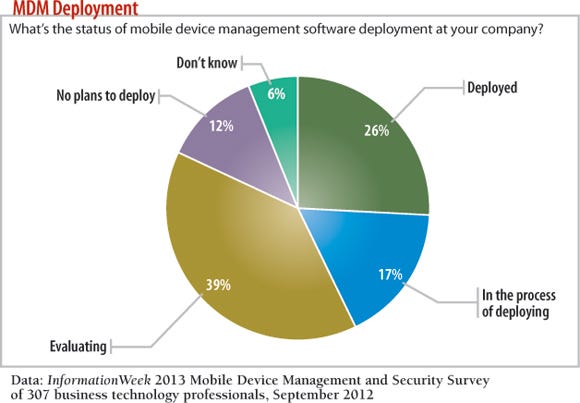
But IT doesn't necessarily see mobile device management software as essential to coping with this proliferation of devices in the workplace. Only 26% of respondents to the InformationWeek Mobile Device Management and Security Survey say their companies have implemented MDM software, and another 17% say they're in the process of deploying it.
Even those companies that have implemented MDM need to make sure their technology and policies really deliver the data security and management efficiency they seek. All MDM software offers the same basic capabilities, such as data wipe and device inventory, so look for additional features that fit with how you use mobile devices. For example, is it a priority for your company to build an app store, or will it need to get hundreds of new people a month on new devices? Buy MDM software optimized to deliver those outcomes.
Too many IT shops are working without this strategic view. They're merely scrambling to meet pressure from the CEO on down to offer BYOD options or increase mobile app access. "Our deployment of mobile solutions is more of a reaction to 'want,' with many of the expected issues from poor planning becoming major issues," laments one of the 307 business technology pros who responded to our survey.
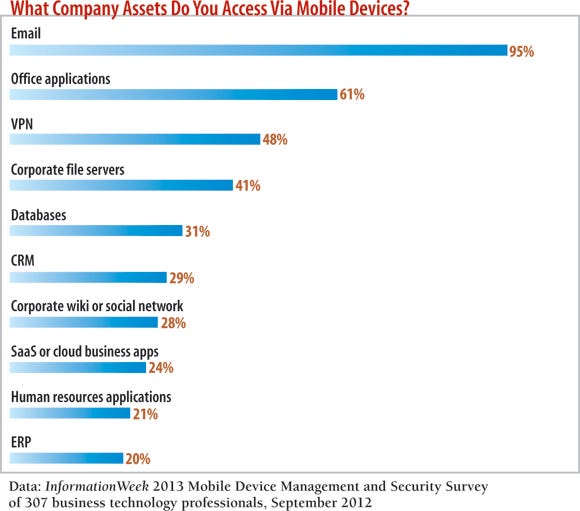
What do employees want to access on their iPhones, Android phones and tablets? The four most-cited resources are email, Microsoft Office applications, VPN and company file servers.
The common trait? Employees need access to corporate data to do work while they're away from the office, and with that data access comes all kinds of security questions: who can access what data, why, when and where -- and what happens when that device goes missing? But mobile data and mobile operating systems present a different security challenge from PCs, which is why just implementing MDM software won't solve IT's BYOD and mobile management headaches. This article spotlights some of the most important factors to consider for those 39% of IT shops now evaluating MDM software -- and even those that don't think they need MDM.
Mobile Is Different
IT organizations first tried to solve the mobile security problem with the same processes they used for laptops and PCs -- tactics such as endpoint protection software, policy enforcement, password complexity and even data leak prevention software. But when your company doesn't own the device (BYOD) or has to deal with hundreds of versions of mobile operating systems, the PC approaches don't cut it.
Review & Analysis: 3 MDM Suites
 Our full report on mobile device management is free with registration.
Our full report on mobile device management is free with registration.
What you'll find:
Three detailed reviews of MDM software suites, from Good Technology, Symantec and Research In Motion
More data on MDM strategy, including goals, platforms supported, vendors used and architectures deployed
MDM software vendors promise to enforce security policies, block employees from installing malicious apps and even encrypt data. But MDM is still young technology. No vendor dominates the market, which includes a mix of legacy security vendors and startups focused entirely on mobile.
Among respondent companies using, planning to use or evaluating MDM, only BlackBerry Enterprise Server and Microsoft ActiveSync are currently deployed or planned for use by more than 14%. Some respondents doubt if MDM even belongs in enterprise IT: Among those who say their companies aren't using MDM, 47% say they have "no need." Says one consultant and former CIO in the survey: "A big reason for BYOD is to get out of the equipment business. If you implement MDM, you are back in the equipment business."
We decided to do a hands-on assessment of MDM products.We sent invitations to more than 20 vendors, but only three agreed to take part. Most of the other vendors said they didn't want to participate until the next versions of their software were available. So when would that software be ready? Crickets.
However, the three vendors that participated -- Good Technology, Symantec and Research In Motion -- are good industry representatives, as each approaches MDM in a different way. Symantec is a security vendor with experience in detecting and mitigating threats in large enterprises. Good uses a secure container approach, replacing the corporate email, calendar and file-sharing applications with its own. Its approach requires employees to learn a different interface, but it's the same across Android and Apple devices. RIM, the newest of the three to vendor-neutral MDM, acquired Ubitexx in 2011 to try to build on its enterprise IT customer base by letting customers deploy non-BlackBerry devices using its management software. We took each vendor's product and deployed it in our lab, with access to normal support but no special engineers or on-site techs.
We tested the products for managing iPad 2, iPhone 4S, Android 2.3, Android-based Samsung Galaxy Tab 7, BlackBerry Bold phone and RIM's PlayBook tablet, where the products supported those devices. We left off Windows Mobile because most vendors don't have full support for those devices -- something to consider if you're a Windows shop. Our three reviews are on the accompanying pages; longer versions plus additional survey data are available in our free report.
Security Is Pretty Much The Same
The main reason companies are turning to MDM software is security, cited by 72% of the respondents to our survey. The other three reasons we provided are greater mobile spending efficiency (12%), inventory/audit (8%) and cost savings (7%).
The security controls for MDM software all do pretty much the same thing, because each mobile device's operating system limits what MDM vendors can do to a device.
Some MDM vendors (including Good) require the user to access email within their application or a partner's application, rather than from the email application provided with the device. This setup lets the MDM vendor enforce certain policies the device's email application doesn't support, particularly encryption and selective email data wiping. All device vendors now allow encryption and wiping, but those features are controlled at the device level. What if you want to wipe company data only and not the phone user's personal pictures? You can do that only if all of the company data is isolated within the MDM vendor's application.
The big limitation of MDM technology has to do with the fact that mobile applications, unlike PC applications, run in sandboxes. For the most part, each mobile application has to specifically request, at install time, the ability to access shared parts of the phone, such as contacts, phone records and other data. If the application doesn't request that type of access at install time, the application is denied access to those areas. It can't be altered later.
The upside to this approach is that it greatly increases mobile device security. Most PC malware and security problems involve an application being compromised by an attacker, and the attacker using that application to access data or another application on the system. It's called "lateral movement" in the security world, and mobile operating systems were architected to prevent those attacks.
This is why most malware needs to jailbreak, or root, the phone to cause real havoc. Without breaking out of the application jail or becoming root, the malware wouldn't be able to access anything on the device.
MDM vendors have the same problem. They can't root or jailbreak your device, but they would like to control the security of the apps on the device. So when they want to add a capability, like remotely wiping data, they have to wait until the mobile operating system allows it. MDM vendors are at the mercy of mobile OS makers such as Apple and Google.
This state of affairs doesn't mean MDM is useless -- quite the contrary. But IT leaders must understand MDM software's inherent limitations. MDM vendors are governed by the same policies and rules as all of your other mobile apps. So those vendors must think of creative ways to get around the mobile operating system security model to improve your phone's security. Kind of odd, isn't it?
There's precedent for such a business model. Antivirus software, for example, uses the same techniques as many kernel malware and rootkits, and it completely violates the Windows kernel architecture, which is why in the early days of antivirus software it was so unstable and caused so many incompatibility problems.
The Features To Watch Closely
So when it comes down to picking the right MDM product for your company, the core security features aren't going to separate one from another. All MDM providers can let you remotely wipe the device, turn features such as the camera on and off, and enforce passcode requirements. The iPhone and Android operating systems pack more than 35 standard policy options, and every MDM vendor implements them.
What makes the difference is all the other stuff, such as deployment capabilities, integration with your environment and ease of use. That's where we focus our product analyses and where you should focus yours. Here are some key factors to consider:
>> Deployments: Assess how efficiently the MDM agent can be deployed on a new device. Deploying new phones isn't a one-time job; it's never-ending. Is your IT team going to face a blizzard of requests, complaints and workarounds every time a new iPhone or Samsung Galaxy comes out? Make sure your tool can keep up.
>> Whitelist and blacklist filtering: You'll have apps that every employee must install, some that are banned and some apps that you insist are updated to at least a certain version. Application filtering and whitelists and blacklists let you control this process based on the device type.
>> Custom app stores: People are trained in their personal lives to use the default Apple or Google app store for their devices, but your company might want to create its own store for in-house custom apps. Apple's and Google's approval processes might take too long for your company, or you may not want your app public. If so, look closely at MDM's support for installing custom, unapproved apps and setting up a company app store experience.
>> App security screening: Apps can be malicious. What is the MDM vendor doing (if anything) to assess apps -- is it offering built-in scanning or application vetting?
>> Browser security: If supported, mobile Web browsing can be filtered to lower the risk of attack on a device. Is the MDM provider you're considering implementing this level of security?
>> Encryption levels: Every device manufacturer supports encryption, but the levels differ. Do you have to encrypt the entire device, or does the MDM provider let you encrypt only company data or specific files and folders?
>> Data wiping: For employees who use their personal phones to access company data, you may want the ability to erase that company data without wiping the entire device. Capabilities vary.
>> Auto-provisioning of devices: If a help desk engineer must spend considerable time with every new mobile device that needs access to company data, it's a recipe for disaster. Look closely at the MDM software's self-service and auto-provisioning capabilities.
>> Architecture: Does the vendor take a sandbox, virtualization or integrated approach? This is important in understanding the vendor's technology and future road map.
>> Location capabilities and network access restrictions: What if you want to let employees use their device's camera for personal use but not when they're at the office? You'll need a policy based on location. Look at whether the MDM software you're considering supports such policies and how robust those policies can be.
>> Inventory management: Once you have hundreds of mobile devices under management, how easy is it to search, find and modify individual devices? Press on the type and rigor of filtering capabilities provided.
>> Reports: Check for built-in reporting in such areas as new devices provisioned, apps out of compliance and devices that haven't checked in for a day or a week.
Data At The Core
The feature our survey respondents want the most is policy setting and compliance, followed by being able to push updates to devices and to remotely wipe data if a device is lost or someone leaves the company. One of the biggest concerns about BYOD and mobile device sprawl is that sensitive company data will leak out, so when assessing MDM suites, follow the data. We looked at where the MDM software's control of company data stops, and what assurances it gives that the device is secured according to company policy.
Since many MDM features are the same across products, ask each vendor what its differentiating features are. For example, Symantec bundles in data loss prevention capabilities -- a challenge because the mobile operating system doesn't provide any native DLP capabilities.
While your IT organization is asking all of these tactical and strategic questions, make sure to ask this final question: Should you even buy MDM, or will the market melt away in two years? As the MDM market matures, operating system vendors are starting to give away MDM-like features. Google says it will provide a level of MDM within Google Apps for free, and Microsoft's updated group policy for Windows 8 supports most MDM feature (though only on Microsoft devices for now).
Some IT leaders still will see MDM as indispensable, given their data security risks and the pressure to offer more apps and device options to employees. But realize that you have options.
All Articles In This Cover Story:

InformationWeek: Dec. 3, 2012 Issue
Download a free PDF of InformationWeek magazine
(registration required)
About the Author
You May Also Like






