Connected Cars Vs. Cybercrime: Tough Fight
Automakers should consider adding real-time intrusion detection and response capabilities, National Highway Traffic Safety Administration says.


9 Innovative Products: Designers Of Things Conference
9 Innovative Products: Designers Of Things Conference (Click image for larger view and slideshow.)
The sophisticated electronic components that are making modern cars safer, greener, and smarter are also making them dangerously vulnerable to cyberattacks.
Dealing with the threat will require automakers to think beyond typical preventive security measures such as encryption, strong authentication, and system segmentation, the National Highway Traffic Safety Administration (NHTSA) said in a report this week.
The report, and two others also released this week, summarizes the NHTSA's research on the security risks raised by the introduction of increasingly complex electronic components in modern cars.
It advocates the need for automakers to consider integrating real-time intrusion detection and response capabilities and methods for quickly extracting, analyzing, and disseminating threat data from compromised systems. Automakers and other industry stakeholders have until Dec. 8 to comment and respond to the report's findings.
[Will Twitter's lawsuit start a trend? Read Twitter Sues US Government Over Surveillance.]
"Our research across other industries indicates that prevention of cyber-threats would be impractical if not impossible," the NHTSA noted in advocating multi-layered defenses for next-generation automobiles.
The Moving Ahead for Progress in the 21st Century Act (MAP-21) requires the NHTSA to review the need for new security and safety standards for electronic systems in passenger vehicles.
As part of that effort, the NHTSA has been directed to review the security implications of new electronic components in automobiles, the interaction of electronic components with other components, and the effect of surrounding environments on the electronic systems in a vehicle.
Figure 1: 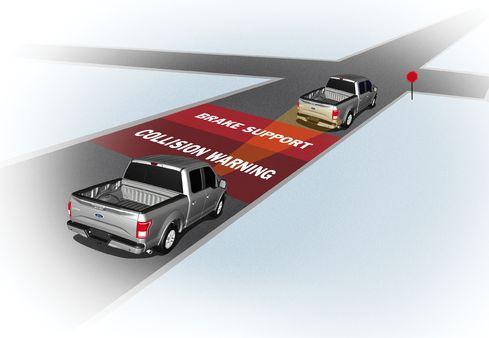 Ford's collision mitigation system uses radar to detect, warn, and, if necessary, activate braking to help drivers avoid collisions with vehicles in front of them. (Source: Ford)
Ford's collision mitigation system uses radar to detect, warn, and, if necessary, activate braking to help drivers avoid collisions with vehicles in front of them. (Source: Ford)
As the NHTSA notes in its report, cars built after 2009 have more than 60 independent electronic control units (ECUs) in them for controlling everything from heating and entertainment systems to steering, braking, and engine-monitoring functions.
Each of these ECUs is accessible either through wired interfaces such as USBs and SD cards or wireless interfaces including Bluetooth, WiFi or near-field communications. Autonomous vehicles like Google's futuristic concept cars are likely to pack a lot more of such components.
The technologies promise to make cars a lot safer and convenient to drive. Vehicle-to-vehicle communication technology for instance, could help reduce crashes by helping drivers maintain an optimal distance from other vehicles at highway speeds.
But like other connected electronic devices, the ECUs in modern vehicles are also vulnerable to accidental or deliberate compromise and manipulation. Security and auto industry researchers fear that the wired and wireless
interfaces in ECUs will give attackers a way to interfere with both the operational and safety equipment in modern vehicles.
Potential attack scenarios run the gamut from attackers tampering with entertainment and temperature control systems to shutting down vehicles at highway speed and taking remote control of critical safety systems.
The concerns are not purely theoretical. In 2013, two researchers at the Defense Advanced Research Projects Agency (DARPA) showed how they could take remote control of a vehicle's steering and brake system by connecting directly to the control area network in the car.
The research prompted one concerned lawmaker to send a letter to the heads of several major automakers asking for details on the measures they are putting in place to mitigate such threats.
Automobile manufacturers will need to take a holistic approach to addressing such concerns, the NHTSA said. The focus should not be just on prevention but also on incident detection and response.
As a complement to preventive measures, automakers should consider technologies that are capable of detecting intrusions into vehicle systems through communication interfaces. Vehicular network communications is fairly predictable and therefore well suited for real-time monitoring and anomaly detection measures, the NHTSA noted.
Automakers should also integrate rapid response capabilities to mitigate the potential harmful effects of an intrusion. The measures could include temporarily shutting down the communication channel that is being exploited, recording and transmitting data back to the automaker for analysis, or simply informing the driver of the risk.
Currently, there are no formal cyber security standards or frameworks that the auto industry can adopt when implementing such measures, the NHTSA acknowledged. But the auto industry can learn and adopt from some of the general cyber security best-practices that are employed in other industries such as the information technology, aviation, financial services, and industrial-control system sectors, the NHTSA said.
Cyber security has become a lifecycle process in all of these industries and many of them have put in place similar standards for the entire supply chain as well.
The automotive-specific guidelines developed by the European Union's E-safety Vehicle Intrusion Protected Applications (EVITA) could also provide a starting point for the US industry to build on, it said.
"Our initial analyses indicate that an automotive sector-specific information-sharing forum... is beneficial to pursue," the agency said, noting that the Alliance of Automotive Manufacturers and the Association of Global Automakers have already embarked on such an initiative.
The Internet of Things demands reliable connectivity, but standards remain up in the air. Here's how to kick your IoT strategy into high gear. Get the new IoT Goes Mobile issue of InformationWeek Tech Digest today. (Free registration required.)
About the Author
You May Also Like






