Montana Health Department Hacked
State of Montana notifies 1.3 million patients of breach to Department of Public Health and Human Services server.

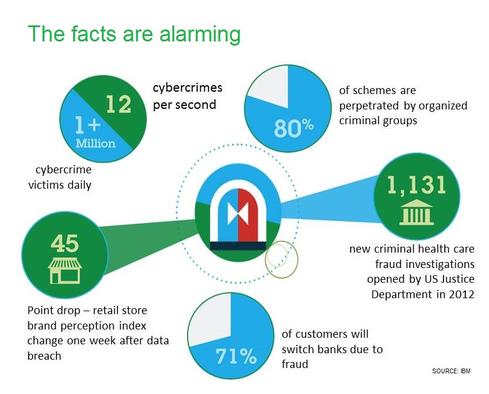
10 Ways To Fight Digital Theft & Fraud
10 Ways To Fight Digital Theft & Fraud (Click image for larger view and slideshow.)
Hackers breached a server in the State of Montana's Department of Public Health and Human Services, prompting officials to notify 1.3 million people of the incident.
There is no evidence this information was used inappropriately -- or even accessed -- but the state is offering free credit monitoring and identity protection insurance to potentially affected individuals, said Richard Opper, DPHHS director. Montana also is alerting family members of deceased patients.
Officials discovered the breach after an independent forensic investigation determined a DPHHS server had been hacked. The department ordered the May 22 investigation from Kroll after DPHHS officials first noticed "suspicious activity" on May 15, Jon Ebelt, DPHHS public information officer, told InformationWeek.
[Researchers discover a flaw in two-factor authentication. Read PayPal Two-Factor Authentication Broken.]
Since the breach, DPHHS has "taken several steps to further strengthen security, including safely restoring all systems affected, adding additional security software to better protect sensitive information on existing servers, and continually reviewing its security practices to ensure all appropriate measures are being taken to protect citizen information," according to the release. For security reasons, DPHHS declined to expand on these additional measures.
Eyal Firstenberg, vice president of cyber research at LightCyber, a security breach detection company:
The time gap between the initial breach and the detection, while outrageously long, is far from being a rare occurrence. In fact, once mission-driven attackers have established a stable beachhead they leverage legitimate existing network resources, like user credentials, for the next phases of the attack. They thus render traditional security controls, like AV, firewalls, and sandboxes useless. With no system in place to monitor the internal network in real-time, attackers are effectively allowed to explore, compromise and exploit the network at their leisure.
The health department notified both Federal Bureau of Investigation and the Montana Attorney General's Office of the breach, said Ebelt.
No information about any potential suspects was available.
Although many healthcare breaches have historically resulted from employee carelessness or error, hackers are increasingly attracted to this industry's rich stash of personal data -- including Social Security numbers, credit card information, and addresses -- and personal health information, experts said. In its 2014 Data Breach report, Verizon determined physical theft and loss, insider misuse, and miscellaneous error accounted for 73% of healthcare breaches.
Michael Raggo, security evangelist at MobileIron, told InformationWeek last month:
I will never say never, but the healthcare industry has seen a disproportionately low instance of cyberattacks, and rather a higher proportion of accidental data loss through well-intentioned but risky user behaviors on the device or lost devices. A major reason for a low instance of cyberattacks is because stringent HIPAA guidelines are a core part of the data security and compliance strategy of all healthcare organizations in the United States. That said, cyberattacks are increasing, as are the number of attack vectors organizations need to protect.
In mid-May, the Office for Civil Rights (OCR) posted 61 new breach incidents affecting more than 500 patients, bringing the 2014 tally to 992 organizations and more than 31,000 patients. More than one third were attributable to theft, and unauthorized access/disclosure accounted for about 15%.
A search of OCR's database reveals only a handful of hacking incidents in 2014. In April, DeKalb Health's website was compromised when the service provider operating the Indiana provider's website was targeted by an overseas hacking group. Hackers created a fraudulent page made to resemble the legitimate site of the DeKalb Health Foundation, a non-profit organization, and sent phishing emails seeking donations. Hackers also defaced DeKalb's website to link to the fake site.
During its investigation, DeKalb discovered that several patient databases were housed on the affected server, notified patients, and provided one year of free monitoring services.
Also in May, Centura Health fell victim to a phishing scam after hackers reportedly targeted employees at the non-profit division of Mercy Regional Medical Center. The organization notified about 1,000 patients whose information may have been compromised when hackers might have gained access to personal information including Medicare beneficiary numbers, Social Security numbers, and dates of birth. An external forensics firm confirmed this data could have been compromised.
Nobody wants to be the next data breach headline. But ensuring that cyber-security defenses are operating effectively and efficiently is a monumental challenge given the sheer volume of information coming at us. Here's how to streamline your program. Get the Metrics That Work: Practical Cyber-Security Risk Measurements report today (registration required).
About the Author
You May Also Like






