4 Essentials For Mobile Device VPNs
VPNs for smartphones and tablets have different requirements than laptops. Here’s what you need to know.


Smartphone Personality Test: Can You Judge Me Now?
Smartphone Personality Test: Can You Judge Me Now? (Click image for larger view and slideshow.)
Smartphones and tablets are now essential workplace tools, but IT and security teams struggle to find the right balance between enabling access and protecting corporate information. This challenge is particularly acute when the company doesn't own the device.
As a result, organizations must stitch together both policies and tools to cover data security requirements. One tool is the mobile VPN, which encrypts traffic between a smartphone or tablet and a corporate gateway.
The encryption prevents information from being snooped while in transit across both wireless and wired networks. It can also help prevent employees and third parties from reaching parts of the corporate network they don't require access to.
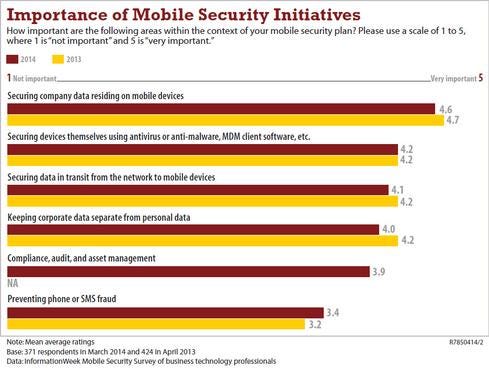
According to InformationWeek's 2014 Mobile Security Survey, securing data in transit is one of the top three initiatives among respondents.
[No one cares about your data like you do. See 3 Enterprise Security Tenets To Take Personally.]
When it comes to choosing a VPN technology, there are four key factors your enterprise should consider.
1. Support for all connection mediums
VPNs should encrypt communications over any type of connection an employee uses to access the corporate network, whether a mobile hotspot, cellular connection, or public WiFi.
In addition, the VPN should provide seamless roaming. This ensures the user doesn't need to re-establish the connection or manually adjust settings when connecting to different mediums, such as moving from a WiFi connection in a café to a cellular service out on the street.
2. Compatibility with multiple operating systems
As the BYOD trend grows, along with the number of device and software options, network administrators will have less control over the operating systems employees use. The InformationWeek Mobile Security survey bears this out: 43% of respondents allow employees to bring in any device, as long as users agree to certain policies. Another 9% allow devices without any restrictions.
This means a VPN should be able to support a majority of the leading operating systems -- Windows, Android, Linux, Apple's offerings, and, ideally, a number of smaller platforms.
3. Policy flexibility
Network administrators may need to adjust backend settings to keep a VPN connection open for a different period of time depending on the user's device.
Say a mobile device goes idle more often than a laptop. Should it disconnect from the VPN tunnel each time to prevent possible third-party infiltration? Or should it remain on, so that it's easier for employees to access the VPN? Administrators need the flexibility to determine the option that best fits their requirements.
4. Interoperability with existing infrastructure
A VPN should be part of a reliable remote access infrastructure, so that the integration of new end devices into the established framework is as seamless as possible. It's important to gather information about how a VPN will operate within whatever infrastructure the company maintains.
If a product doesn't mesh with an existing network security framework, then it's not going to be of much value. As more advanced threats proliferate, interoperability between network and security components is vital.
It takes more than just a VPN to protect mobile devices and corporate data. But VPNs used in conjunction with mobile device management, access control, and application management, as well as an educated employee base, will go a long way to reducing the risks presented by mobile devices.
How cloud, virtualization, mobility, and other network-altering trends impact security -- and the IT pros responsible for infrastructure protection. Get the Network Security Career Guide issue of Network Security today.
About the Author(s)
You May Also Like






