iOS Mail App Vulnerable To Phishing Bug
An unpatched bug in Apple's Mail app for iOS mobile devices could easily fool users into giving up their iCloud passwords to phishing hackers.

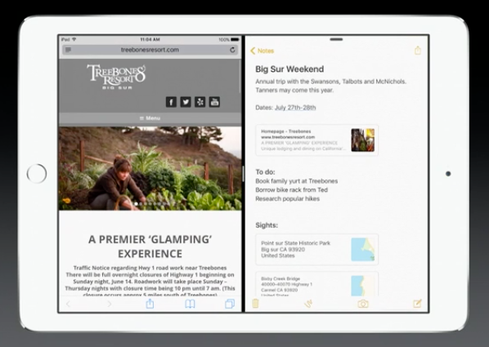
5 Apple Features We've Seen Elsewhere
5 Apple Features We've Seen Elsewhere (Click image for larger view and slideshow.)
Although Apple prides itself on consumer security, an Ernst & Young security researcher says he has discovered a flaw in iOS 8.3's email app that could result in stolen passwords from iCloud.
Researcher Jan Soucek published a proof of concept tool that exploits the operating system's Mail application in a savvy enough way that most users would be unaware of the bug.
"This bug allows remote HTML content to be loaded, replacing the content of the original email message," the post on GitHub explained. "JavaScript is disabled in this UIWebView, but it is still possible to build a functional password 'collector' using simple HTML and CSS."
Soucek explains that the code detects that the research subject has already visited the page in the past by using cookies and it stops displaying the password prompt to reduce suspicion.
Soucek uses the login to iCloud just as a demonstration -- any random HTML and CSS could run, not just a prompt warning of a potential phishing risk.
To make matters worse, the password field then has autofocus enabled, to mimic Apple's official password prompt, making it appear as though everything is in official order.
"The safe course for now is to assume that any login popup that appears while using the iOS Mail app is malicious," Apple-centric blog 9to5Mac wrote. If your iOS device does indeed need you to login again to iCloud or anything else, wait until prompted when not using Mail.
The Github page also provides a link to a one-minute YouTube video that explains how the exploit works visually.
"Back in January 2015 I stumbled upon a bug in iOS's mail client, resulting in HTML tags in email messages not being ignored," Soucek writes. "It was filed under Radar #19479280 back in January, but the fix was not delivered in any of the iOS updates following 8.1.2. Therefore I decided to publish the proof of concept code here."
Michael Oh, chief technology officer and founder of TSP, a team of Apple specialists, told InformationWeek that while it's not a "serious" security flaw in terms of the device data being compromised, it's serious because it's part of a new generation of security issues that are a combination of social engineering and cloud services.
"Knowing someone's iCloud password is a gateway to huge amounts of data -- their contacts, their calendar, their personal email, photos, even being able to purchase things," he explained. "It won't catch advanced users, but it could catch pretty much anyone else."
[Read about the original iCloud celebrity hack.]
Oh also noted it would be interesting to see if it's really seen in the wild, as that would require someone to harvest iCloud.com emails and target people specifically.
"My guess is rather than a huge [phishing] campaign, it's likely to be used by more targeted hackers who are going after specific people -- celebrities and their naked pics, for instance," Oh said.
Following the iCloud hacking scandal that targeted a number of celebrities in the fall of last year, Apple quickly created a guide to ensure its users could ensure they were visiting the genuine iCloud page.
According to a report in the Chicago Sun-Times, which obtained a still-sealed affidavit, a flagged IP address led FBI agents to a Chicago South Side home in search of the hacker and spawned a deep-seeded investigation into how the breach occurred.
"The unique computer IP address at the home on Washtenaw was used to access 572 unique iCloud accounts between May 31, 2013 and Aug. 31, 2014, according to one affidavit," the paper reported. "In total, the agent said those accounts were accessed 3,263 times."
About the Author
You May Also Like






